📚 Looking Back at the Zero Day Initiative in 2019
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
Now that we’ve completed our first-ever Pwn2Own Miami, it’s time to reflect on 2019 and the work done by the ZDI. It was another busy year for us. It’s been an incredible year for the program. We introduced an automotive category to Pwn2Own Vancouver, saw UAC abused for privilege escalation, had the Samsung handset exploited via baseband for the third Pwn2Own Tokyo in a row, and disclosed a significantly impactful SharePoint bug later seen in active attacks – and that’s just a few of the highlights. We awarded more than $1.5 million in cash and prizes throughout 2019, and if January is any indicator, 2020 will be an amazing year as well.
Of course, our program relies on external contributors, and we couldn’t do our job without the input and talent of our global community of independent researchers. Their work and submissions are key to our success, and we thank them for their continued trust in our program. Our program also wouldn’t work without vendors generating and releasing fixes for the vulnerabilities we report to them. The ZDI would not be able to sustain this level of advisories – and thus, better protections for Trend Micro customers – without the contributions of researchers and vendors, and we thank them for all they do.
By the Numbers
As of now, the ZDI has published 1,035 advisories for 2019. We usually see notifications from vendors early in the new year of vulnerabilities patched late in the previous year (but where advisories were not coordinated). Because of this, the actual number of 2019 advisories will eventually increase. We’ll update this blog with the final numbers when we have them. Here’s how that number of advisories stacks up year-over-year.
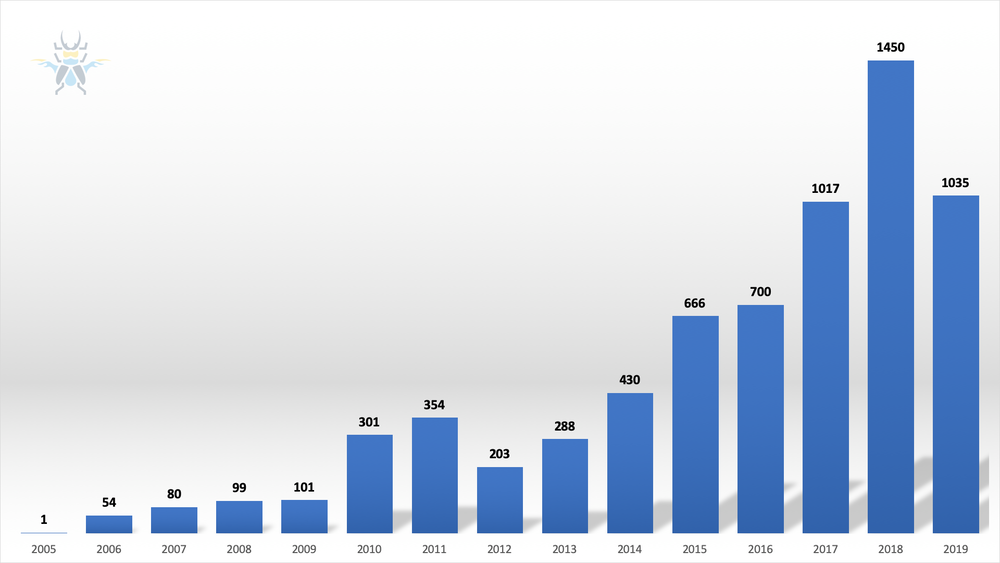
Figure 1 - Advisories published from 2005 through 2019
You’ll notice the total advisories published are down from last year. That doesn’t mean we were any less busy, or that there were fewer bugs coming into the program. If anything, 2018 was a slight aberration, with multiple vendors having more than 200 advisories. Programmatically, we have shifted our focus to reports with greater impact. This is reflected in the CVSS scores of the published advisories, which show a shift from medium to high severity.
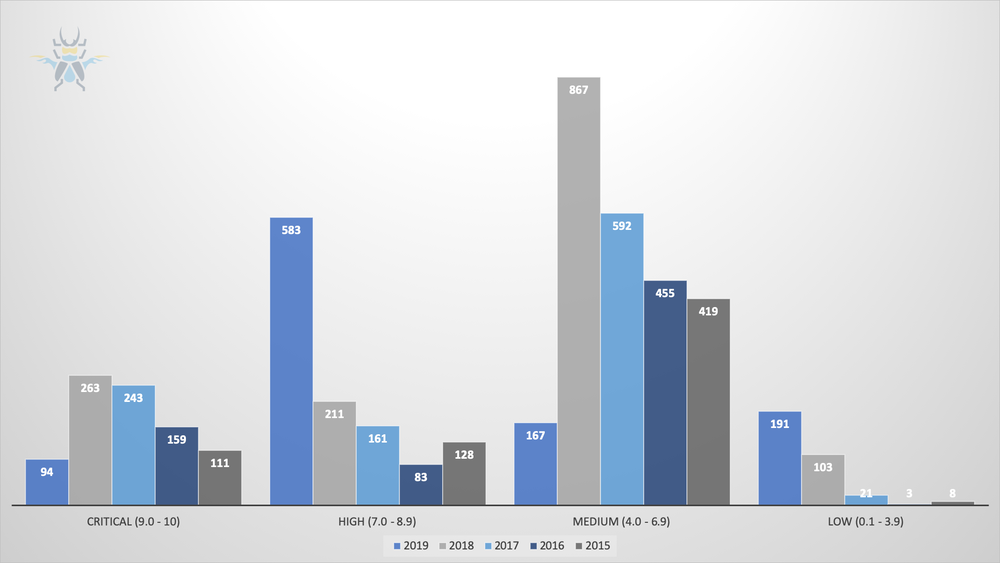
Figure 2 - CVSS scores of published advisories from 2015 through 2019
The increase in low-severity CVSS cases reflects our commitment to information disclosure cases. On their own, they aren’t as impactful. However, when combined with other vulnerabilities, they become an essential piece of an exploit chain. As exploits often rely on info leaks for sandbox escapes and other compromises, these humble info disclosure bugs will continue to be worth purchasing.
Coordinated disclosure of vulnerabilities continues to be a successful venture. A total of 88% of 2019 advisories were published in conjunction with a fix from the vendor. This is in line with disclosure rates from the last few years. The sector that has the most difficulty meeting our disclosure timelines continues to be ICS/SCADA vendors, but perhaps events like Pwn2Own Miami and continued outreach can help change that in 2020.
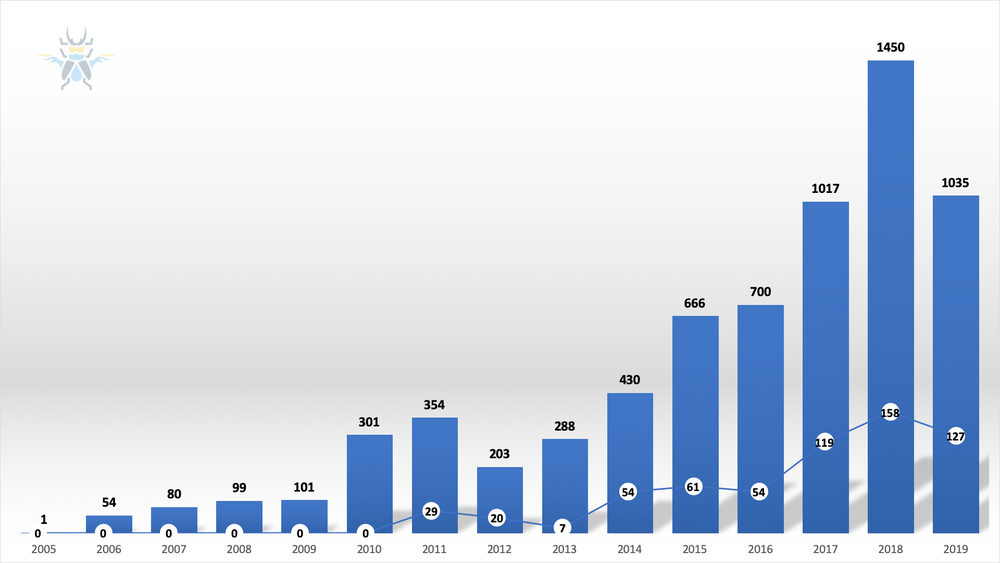
Figure 3 – Portion of published ZDI advisories with no vendor fix available, by year
Looking at the distribution of vendors affected by our advisories, you’ll notice some familiar names at the top of that list:
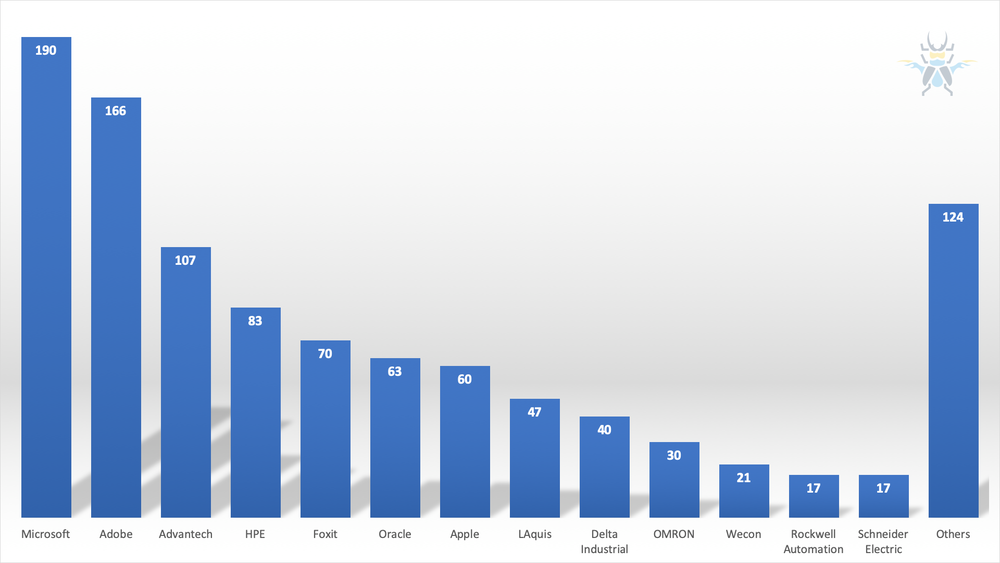
Figure 4 - Advisories per vendor for 2019
In years past, many of the Microsoft bugs we purchased were browser related. We’re still buying plenty of those, but this year saw an increase in bugs affecting the OS as well. In particular, we had an increase in bugs impacting font parsing – both in the kernel and in the GDI+ library. The JET database engine also proved to be a popular target for researchers. Similarly, bugs in Adobe software used to be synonymous with Flash, but that’s no longer the case. In 2019, 2 out of 3 Adobe bugs we purchased impact Acrobat and Reader. We did purchase a few Flash bugs, but we actually had more submissions for Photoshop than we did for Flash – five times more. This year also saw an increase in the amount of ICS/SCADA bugs submitted to the program. A little more than 30% of the published advisories were related to an ICS product in some form.
Techniques and Trends
When looking through the submissions, we definitely saw a few trends when it came to root cause as described by the Common Weakness Enumeration (CWE). Here’s a breakdown of the most popular CWEs from 2019:
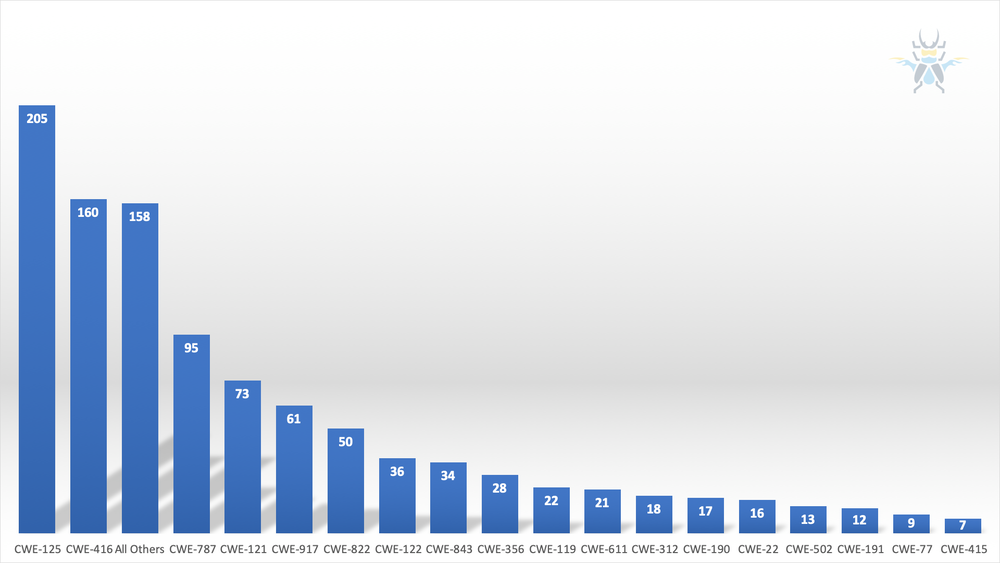
Figure 5 - CWEs of published advisories in 2019
The most popular category shouldn’t really be a surprise. CWE-125 (Out-of-bounds Read) is by far the most common CWE we see. CWE-416 Use-After-Free (UAF) is also quite prevalent, even though it’s a widely understood problem. OOB Writes (CWE-787) occur less frequently than OOB Reads, but still occur with regularity. Stack-based buffer overflows (CWE-121) were submitted more frequently than heap-based overflows (CWE-122). CWE-917 - Improper Neutralization of Special Elements used in an Expression Language Statement (‘Expression Language Injection’) is a mouthful to say, but it still shows up in ~6% of submissions.
These numbers do not necessarily show what types of bugs are being exploited in the wild. There are many types of bugs used by attackers that the ZDI does not purchase. For example, we don’t typically purchase cross-site scripting (XSS), DLL planting, vulnerabilities in live websites or online tools, or ActiveX bugs. Still, looking at the distribution of CWEs in our advisories provides an interesting glimpse into what researchers are finding across multiple products and categories.
Looking ahead
If the past few years are any indication, 2020 will exceed our expectations in ways we cannot predict. We’re already at 154 published advisories for the year (including a couple of 0-days), with advisories covering Oracle, Cisco, Apple, Microsoft, and more. Our own researchers will continue to be busy, as well. In 2019, 20% of the advisories were cases submitted by ZDI researchers. When they aren’t reviewing submissions, ZDI researchers are usually found hunting their own bugs.
The past year saw an across-the-board increase in deserialization bugs, whether they were submitted to the program, used at Pwn2Own, or found in the wild. This trend will likely continue in 2020, although it is unlikely these will reach the level of OOB Reads. It’s certainly something we’ll keep an eye on throughout the upcoming year. We published more than 60 blogs last year, and we hope to keep that pace up this year as well. Expect patch blogs, exploit demonstrations, and more from the MindShaRE series. We’ll also be blogging more about what exploits and trends we’re detecting in the wild. In other words, 2020 is shaping up to be an exciting year with fantastic research, great contests, and information you can use. We hope you join us. Until then, be well, stay tuned to this blog, subscribe to our YouTube channel, and follow us on Twitter for the latest updates from the ZDI.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren