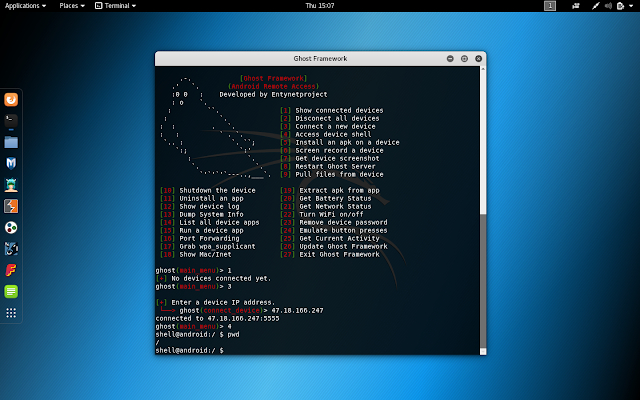
📚 Ghost Framework - An Android Post Exploitation Framework That Uses An Android Debug Bridge To Remotely Access A n Android Device
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
Ghost Framework is an Android post exploitation framework that uses an
Android Debug Bridge to remotely access an Android device. Ghost Framework
gives you the power and convenience of remote Android device administration.Getting started
Ghost installation
cd ghost
chmod +x install.sh
./install.sh
Ghost uninstallation
cd ghost
chmod +x uninstall.sh
./uninstall.sh
Ghost Framework execution
To execute Ghost Framework you
should execute the following command.ghost
Why Ghost Framework
- Accessing device shell.
Ghost Framework can be used to access the remote Android
device shell without using OpenSSH or other protocols.- Emulating device button presses.
Ghost Framework can be used to emulate
button presses on the remote Android device.- Removing device password.
Ghost Framework can be used to remove the remote
Android device password if it was forgotten.Usage of the Ghost Framework for attacking targets without prior mutual consent is illegal.
It is the end user's responsibility to obey all applicable local, state, federal, and international laws.
Developers assume no liability and are not responsible for any misuse or damage caused by this program.

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren