📚 Pwn2Own Day Two – Results and Master of Pwn
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
The final day of Pwn2Own 2020 came to a close yesterday, but not before a bit of drama, intrigue, and more great research. We saw two successful attempts, which resulted in four new bugs earning $90,000. That brings the two-day total to $270,000. Here’s a quick recap of Day Two and the entire event:
Our day began with returning Pwn2Own veteran Phi Phạm Hồng (@4nhdaden) of STAR Labs (@starlabs_sg) targeting Oracle VirtualBox in the Virtualization category. It took all three attempts for a successful demonstration, which heightened the drama, but his third attempt worked like a charm. He combined an info leak & an uninitialized variable to execute code on the host OS from the guest OS. This earned him $40,000 and four points towards Master of Pwn.
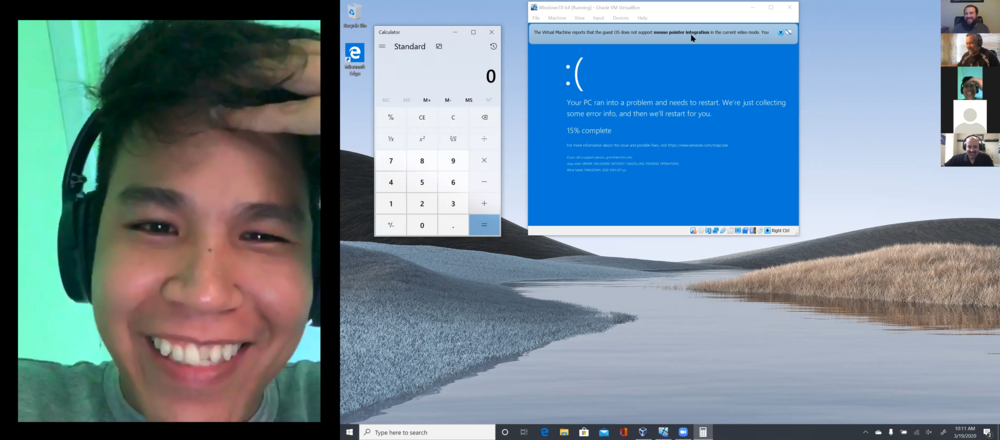
Figure 1 – Phi Phạm Hồng of STAR Labs watches his Oracle exploit succeed
Next up, the Fluoroacetate duo of Amat Cama and Richard Zhu returned for their second event of the competition. This time, they had their sights set on Adobe Reader. In one of the most impressive displays of the competition, they leveraged UAFs in Reader and Windows kernel to escalate to SYSTEM. All it took was opening a PDF and the entire system was compromised. This impressive display earned them another $50,000 and 5 more points towards Master of Pwn.
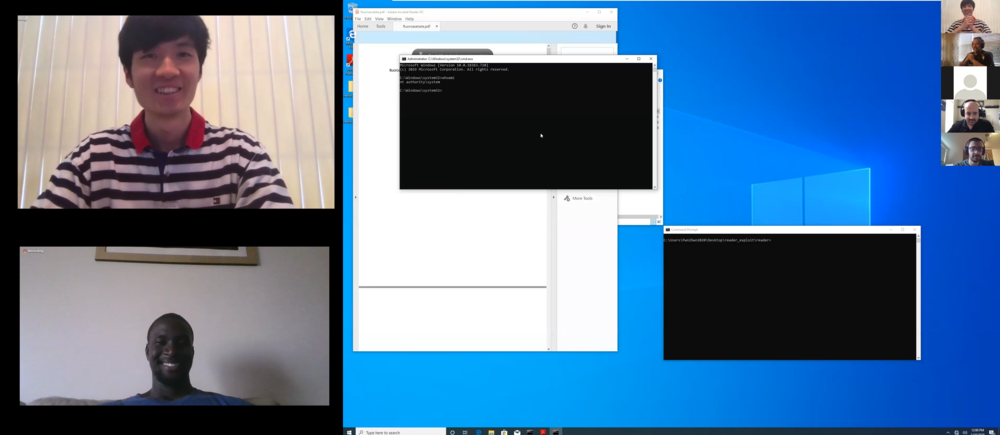
Figure 2: The Fluoroacetate duo of Richard Zhu (top) and Amat Cama exploit Adobe Reader
In the final official entry of Pwn2Own 2020, the Synacktiv team of Corentin Bayet (@OnlyTheDuck) and Bruno Pujos (@BrunoPujos) targeted VMware Workstation with a guest-to-host escape. Unfortunately, they could not successfully demonstrate their exploit in the allotted time. However, upon disclosure, we did find the bug to be valid and purchased it through the regular ZDI program. We hope to see more from these researchers in the future.
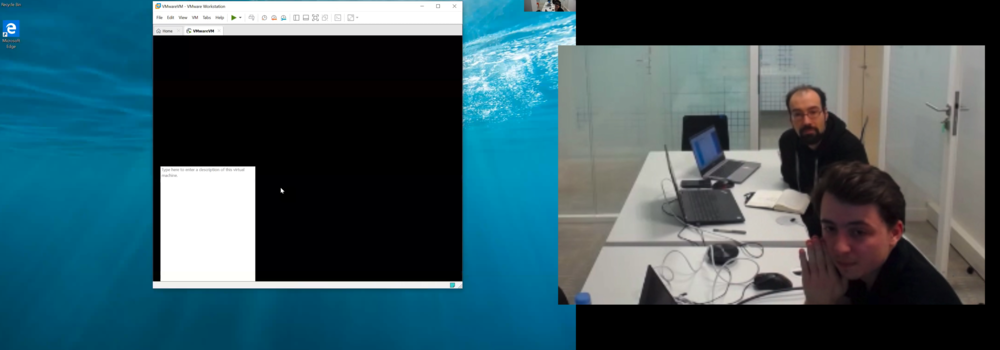
Figure 3 - The Synactiv team of Bruno Pujos (top) and Corentin Bayet
In a special bonus feature, ZDI’s own Lucas Leong (@_wmliang_) demonstrated a guest-to-host escape in Oracle VirtualBox. He leveraged an out-of-bounds read for an info leak and a use-after-free for code execution. You can watch a video of the demonstration on our YouTube channel.
That brings to a close this year’s event. As always, vendors have received the details of these bugs and vendors of Pwn2Own-awarded bug reports have 90 days to produce security patches to address the issues we reported. Once these are made public, stay tuned to this blog for more details about some of the best and most interesting research we saw this week.
It was a tighter race than previous years, but Richard Zhu and Amat Cama of Fluoroacetate again were crowned the Master of Pwn. In addition to the trophy and custom hockey jerseys, they receive 65,000 ZDI reward points, which gives them Platinum status.

Figure 4: Final Master of Pwn standings
Special Thanks
We wanted to be sure to thank everyone who participated in this year’s competition. There were definitely hurdles to clear, but everyone was accommodating and worked with us to make Pwn2Own 2020 happen. We want to thank the participants for trusting us with their research and allowing us to run each attempt. We want to thank Microsoft, VMware, Apple, Adobe, and Canonical for dialing in throughout the disclosure process. Their continued involvement in coordinated disclosure and security response processes helps the entire community. Special thanks also go out to our partners Microsoft and Tesla and sponsor VMware for their support and assistance before and during the contest.
The world right now is a tumultuous place full of uncertainty. It is communities, such as the security research community and the incident response community, that we can rely on during these trying times. We are so appreciative of all those who helped the event come together and succeed. We’ll get through this together, and we hope to see you again at our next event. Until then, you can follow the team for the latest in exploit techniques and security patches.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren