📚 Announcing Pwn2Own Tokyo 2020 – Live from Toronto!
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
If you just want to read the rules, you can find them here.
Over the past few years, our Fall Pwn2Own contest has been held at the PacSec Applied Security Conference in Tokyo, Japan. This year, PacSec will be held virtually, so we began to look at how we could do a virtual Pwn2Own Tokyo similar to how we held our Spring event. Pwn2Own Tokyo typically focuses on devices like mobile phones, televisions, smart speakers, and wireless routers – physical devices that make it problematic to go completely virtual. However, the Zero Day Initiative (ZDI) has a large team of researchers in our Toronto office, which provides us a perfect setting to hold the contest. For 2020, our Pwn2Own Tokyo event will come to you live from Toronto and coincide with the virtual PacSec Conference, which is currently scheduled for November 1-6, 2020. We'll be holding the competition on November 3-5, 2020. We’ll have 20 devices available as targets and be offering more than $500,000 USD in prize money.
Similar to how we conducted our Spring Pwn2Own event, we will allow remote participation in this year’s Pwn2Own Tokyo event. If you have either travel restrictions or travel-safety concerns, you can opt to compete remotely. You will still need to register before the contest deadline (October 29, 2020) and submit a detailed whitepaper completely explaining your exploit chain and instructions on how to run the entry by November 1, 2020. A member of the ZDI staff in Toronto will run the exploit for you. All attempts will be filmed and available for viewing by the contestant and the vendor. If requested, we will work with remote contestants to monitor the attempt in real-time via a phone call or video chat. Please note that since you are not in person, changes to exploits/scripts/etc. will not be possible, which could lower your chance of winning should something unexpected occur.
Otherwise, the contest will run as though we were in Tokyo. We will have a random drawing to determine the schedule of attempts on the first day of the contest, and we will proceed from there. Our intention with allowing remote participation is to provide as many people as possible with the benefits of participating in Pwn2Own while still treating all contestants as equally as possible. If you have questions about this remote participation option, please contact us at zdi@trendmicro.com. We will be happy to address your questions or concerns directly.
As for the contest itself, we’re happy to announce Facebook returns as a partner for this year’s event, again offering Oculus Quest and Portal from Facebook devices return as targets. No one targeted either device during their inaugural show, so it will be interesting to see if anyone targets them this year. Vendor participation remains a key component to the success of these contests. As with our other Pwn2Own competitions, Pwn2Own Tokyo (Live from Toronto) seeks to harden these consumer-focused devices and their operating systems by revealing vulnerabilities and providing that knowledge to the vendors. As always, the goal is to get these bugs fixed before they’re actively exploited.
The Target Handsets
At its heart, Pwn2Own Tokyo (once known as Pwn2Own Mobile) looks at mobile phones, and this year is no different. Here are the target handsets for Pwn2Own Tokyo 2020:
- Google Pixel 4
- Samsung Galaxy S20
- Apple iPhone 11
- Huawei P40
- Xiaomi Mi 10
As usual, all these phones will be running the latest version of their respective operating systems with all available updates installed.
Smart Speakers, Wearables, Network Attached Storage, Televisions, and More
Over the past few years, we’ve been expanding the targets to include more than just mobile phones. Last year, we introduced wireless routers and televisions into the mix. This year, we expand once again by including Network Attached Storage (NAS) servers. Here’s the full list of all devices included in this year’s event:
Wearables:
- Apple Watch Series 5
- Oculus Quest (64Gb)
Home Automation:
- Portal from Facebook
- Amazon Echo Show 8
- Google Nest Hub Max
- Sonos One Speaker
- Nest Cam IQ Indoor camera
- Ring Indoor Cam
- Arlo Q Plus Indoor camera
Televisions:
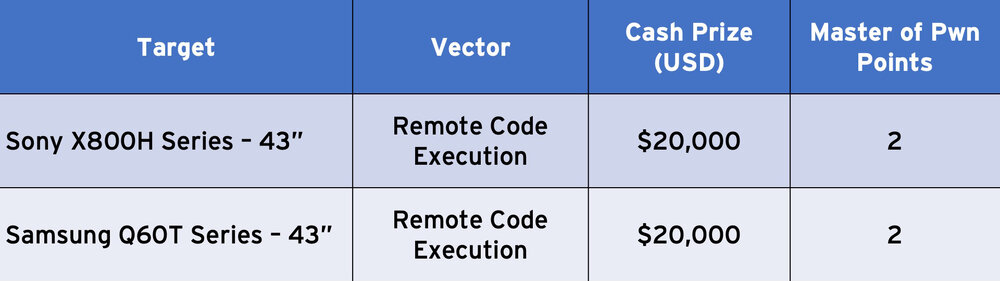
- Sony X800H Series - 43”
- Samsung Q60T Series – 43”
Routers:
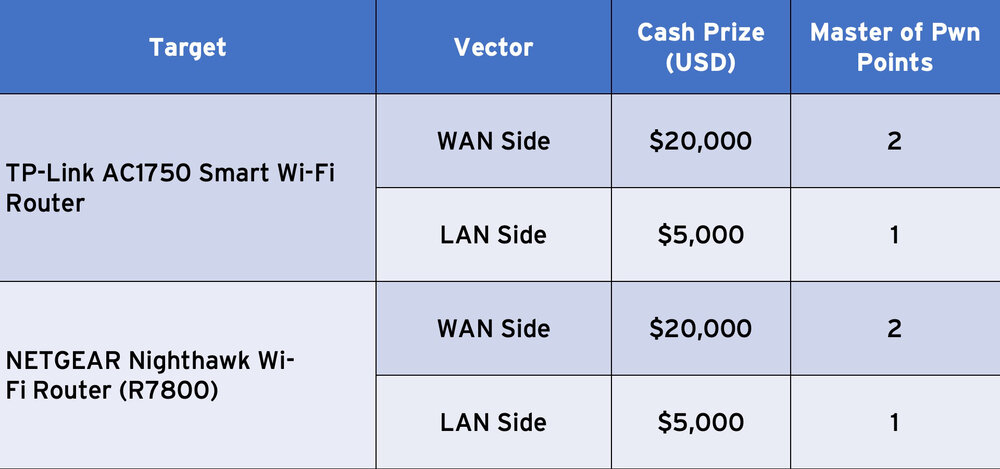
- TP-Link AC1750 Smart Wi-Fi Router
- NETGEAR Nighthawk Smart Wi-Fi Router (R7800)
NAS Server:
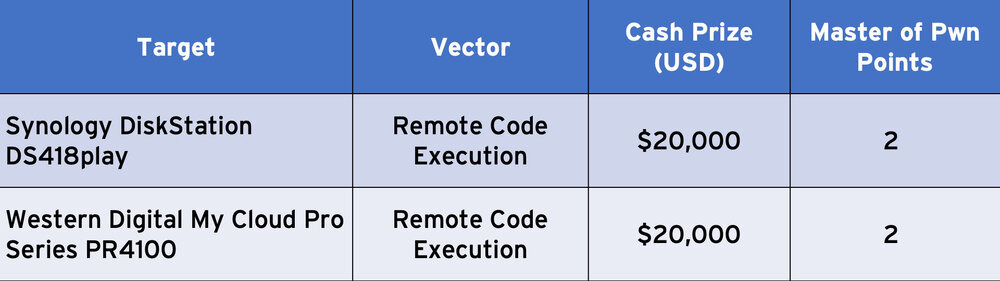
- Synology DiskStation DS418play
- Western Digital My Cloud Pro Series PR4100
As with the phones, all these devices will be updated to the most recent patch level or system update, and all will be in their default configuration.
The Pwn2Own Tokyo (Live from Toronto!) Challenges for 2020
Now that you know the devices available, let’s look at the different categories of challenges, starting with the various tests against mobile handsets.
Web Browser Category
In this category, contestants will target the default web browser of each particular handset. The awards for this category are:
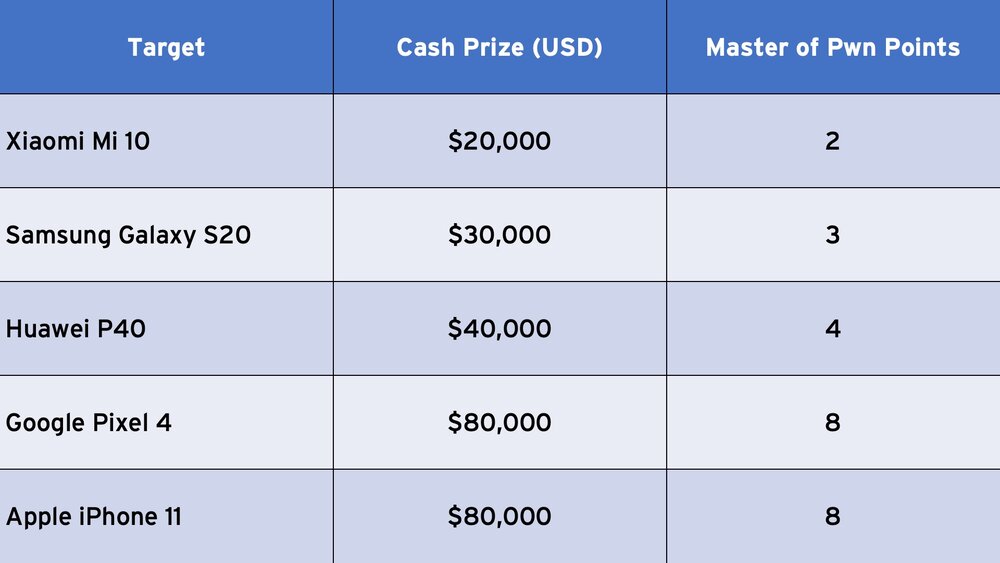
This category also includes add-on bonuses for some of the handsets. If your exploit payload executes with kernel privileges on any of these handsets, you will earn an additional $30,000 and 3 more Master of Pwn points. There will also be a bonus for the exploit payload surviving a reboot. Accomplish this on the Google Pixel or either iPhone and you earn another $50,000 and 5 Master of Pwn points. That means a full iPhone or Pixel browser exploit with persistence and kernel-level access will earn $160,000.
Short Distance Category
In this category, contestants will target the phones over one of the following short distance protocols: Bluetooth, Wi-Fi, or near field communication (NFC). The awards for this category are:
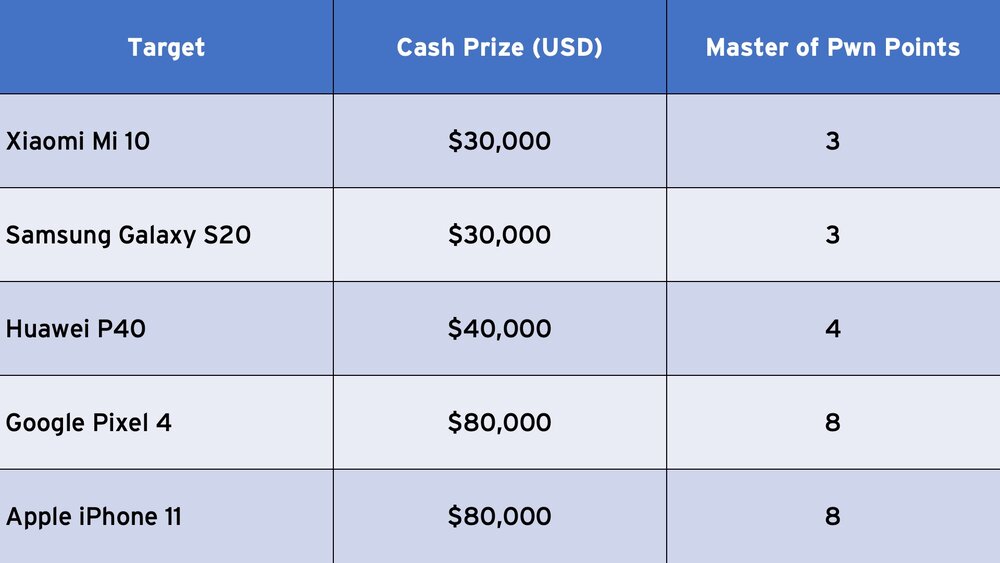
This category also has the same add-on bonuses as the browser category. That means another $30,000 and 3 Master of Pwn points for a kernel-level exploit, and $50,000 and 5 Master of Pwn points for persistence on the Google Pixel or Apple iPhones.
Challenges Involving Other Devices
This is our third year of including IoT, wearable, and other hardware devices, and each year brings new research that exceeds our expectations. Last year, we saw the Amazon Echo compromised. This year, we’re bringing even more smart speakers and introducing NAS servers to the mix. It should be interesting.
For the devices at Pwn2Own Tokyo that aren’t mobile handsets, a successful entry will compromise the device and retrieve some form of sensitive information. For some of these challenges, local privilege escalations are in scope but result in a lower award.
Wearables
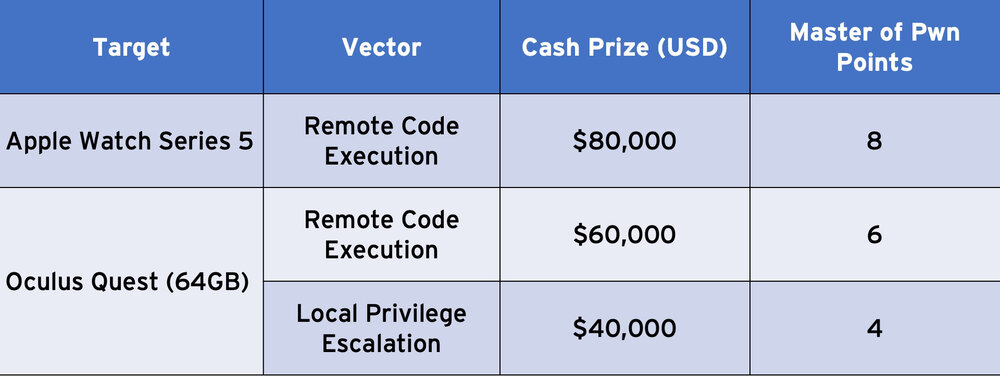
Home Automation Category
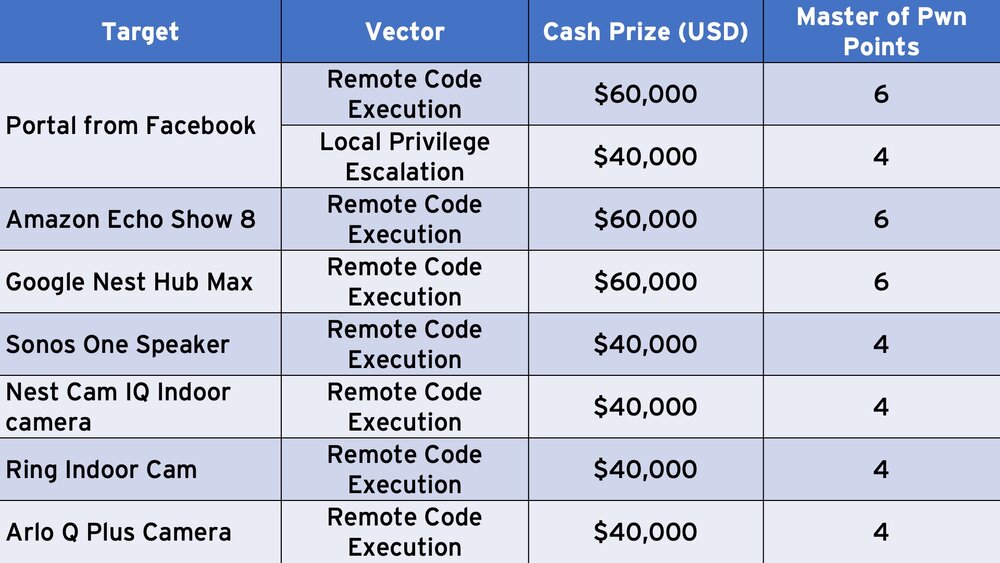
Television Category
Wireless Router Category
For this category, contestants may target either the WAN or the LAN interface.
NAS Category
Master of Pwn
No Pwn2Own contest would be complete without crowning a Master of Pwn, which signifies the overall winner of the competition. Earning the title results in a slick trophy, a different sort of wearable, and brings with it an additional 65,000 ZDI reward points (instant Platinum status in 2021).
For those not familiar with how it works, points are accumulated for each successful attempt. While only the first demonstration in a category wins the full cash award, each successful entry claims the full number of Master of Pwn points. Since the order of attempts is determined by a random draw, those who receive later slots can still claim the Master of Pwn title – even if they earn a lower cash payout. As with previous contests, there are penalties for withdrawing from an attempt once you register for it. If the contestant decides to remove an Add-on Bonus during their attempt, the Master of Pwn points for that Add-on Bonus will be deducted from the final point total for that attempt. For example, someone registers for the Apple iPhone 11 in the Browser category with the Kernel Bonus Add-on. During the attempt, the contestant drops the Kernel Bonus Add-on but completes the Browser attempt. The final point total will be 5 Master of Pwn points.
The Complete Details
The full set of rules for Pwn2Own Tokyo 2020 is available here. They may be changed at any time without notice. We encourage entrants to read the rules thoroughly and completely should they choose to participate.
Registration is required to ensure we have sufficient resources on hand at the event. Please contact ZDI at zdi@trendmicro.com to begin the registration process. (Email only, please; queries via Twitter, blog post, or other means will not be acknowledged or answered.) If we receive more than one registration for any category, we’ll hold a random drawing to determine contestant order. Registration closes at 5:00 p.m. Eastern Daylight Time on October 29, 2020.
The Results
We’ll be blogging and tweeting results in real-time throughout the competition. Be sure to keep an eye on the blog for the latest results. Follow us on Twitter at @thezdi and @trendmicro, and keep an eye on the #P2OTokyo hashtag for continuing coverage.
We look forward to seeing everyone in Tokyo Toronto (or online), and we look forward to seeing what new exploits and attack techniques they bring with them.
With special thanks to Pwn2Own Tokyo 2020 partner Facebook for providing their technology:

©2020 Trend Micro Incorporated. All rights reserved. PWN2OWN, ZERO DAY INITIATIVE, ZDI, and Trend Micro are trademarks or registered trademarks of Trend Micro Incorporated. All other trademarks and trade names are the property of their respective owners.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren