📚 Pwn2Own Tokyo (Live from Toronto) - Day One Results
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
The first day of Pwn2Own Tokyo 2020 (Live from Toronto) is in the books, and some fantastic research was put on display. The first day of the contest saw us award $50,000 for seven bugs in four different products. Here’s a quick recap video of the day’s proceedings:
As always, our contest began with a random drawing to determine the order of attempts. We have 19 entries from 12 different groups for this year’s event. With the schedule established, we were on our way.
Our first attempt saw the STARLabs team target the LAN interface on the NETGEAR Nighthawk R7800 router. They wasted no time and were able to use a pair of bugs to get their code execution going. They completely compromised the router, which earned them $5,000 and 1 point towards Master of Pwn.

Figure 1 - The STARLabs team wasted no time in demonstrating their exploit
Next up, the Trapa Security team targeted the Western Digital My Cloud Pro Series PR4100. This was the first time a NAS server had been targeted at a Pwn2Own event. The team didn’t disappoint as they used an authorization bypass and a command injection bug to take over the server. The successful demonstration earned them $20,000 and 2 points towards Master of Pwn.
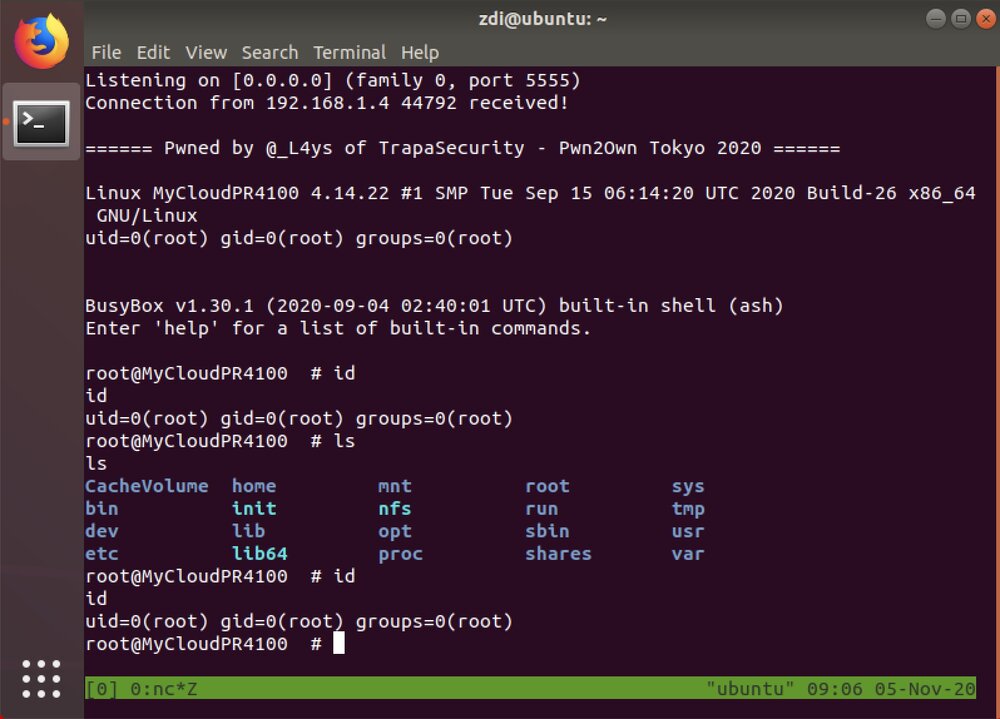
Figure 2 - The Trapa Security team showing off their root shell
Pwn2Own veterans Team Flashback were next. This time, they were targeting the WAN interface of the NETGEAR Nighthawk R7800 router. Not only did they use a two-bug chain to compromise the router, they were able to leave a back door in the router that would persist even through a factory reset. The demonstration earned them $20,000 and 2 Master of Pwn points.

Figure 3 - Team Flashback celebrates another successful exploit
Next, Pwn2Own newcomer 84c0 successfully demonstrated remote code execution against the Western Digital My Cloud Pro Series PR4100. Unfortunately, the bug he used had been previously reported. This still counts as a partial win but does not receive any points towards Master of Pwn.

Figure 4 - 84c0 watches his exploit yield root access on a Western Digital NAS
The following attempt was fraught with drama, as the Black Coffee team could not get their exploit to work with the allotted timeframe. The team in Toronto coordinated troubleshooting with Chris and Mike as best they could – including swapping hardware in the middle of the attempt. It just wasn’t happening for the Black Coffee team today.

Figure 5 - Team Black Coffee was unable to demonstrate their exploit in the time allotted
The first television targeted in this year’s contest was the Samsung Q60T. The Viettel Cyber Security team was able to get a reverse shell on a fully patched device. However, the bug they used was previously known. This still counts as a partial win and nets them one point towards Master of Pwn.

Figure 6 - The Viettel Cyber Security team watches their reverse shell succeed on the Samsung TV
The final demonstration for Day One saw the Trapa Security team return to target the LAN interface on the NETGEAR Nighthawk router. Their command injection bug needed little time to completely take over the device. The exploit earned them another $5,000 and one more point towards Master of Pwn.
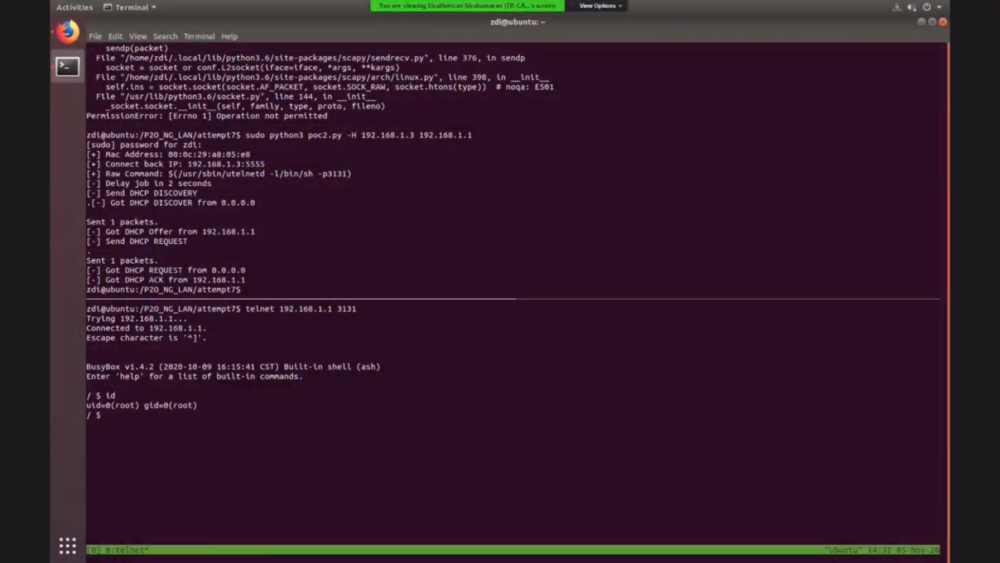
Figure 7 - The Trapa Security team showing root access on the NETGEAR router
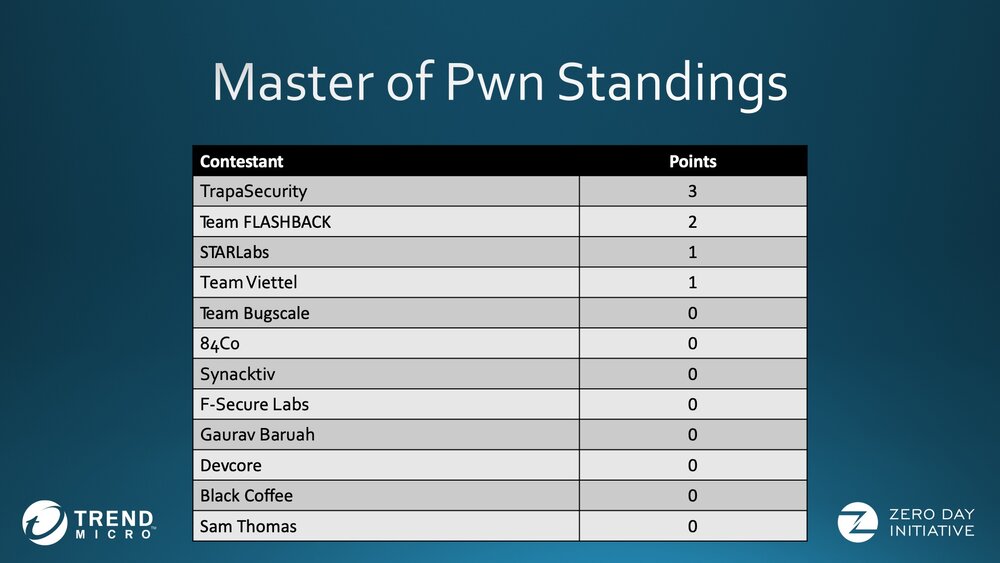
That wraps up the first day of Pwn2Own Tokyo (Live from Toronto) for 2020. With their two successful attempt, Trapa Security is currently in the lead for Master of Pwn.
Join us on Day Two of the contest, which starts November 6 at 10:00 Eastern. As with today, we’ll be Tweeting and updating the blog with results as they occur.
Stay tuned to our Twitter feed and this blog for tomorrow's results as we wrap up this year’s edition of Pwn2Own.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren