📚 NtHiM - Super Fast Sub-domain Takeover Detection
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
NtHiM - Super Fast Sub-domain Takeover Detection
Method 1: Using Pre-compiled Binaries
The pre-compiled binaries for different systems are available in the Releases page. You can download the one suitable for your system, unzip the file and start using NtHiM.
Method 2: Using Crates.io
NtHiM is available on Crates.io. So, if you have Rust installed on your system, you can simply install NtHiM with the following command:
cargo install NtHiMMethod 3: Manual Build
You will need Cargo to perform the manual build for NtHiM. If you have Cargo installed, you can simply follow the steps below:
- Clone this repository,
git clone https://github.com/TheBinitGhimire/NtHiM; - Go inside the folder,
cd NtHiM; - Use the
cargo buildcommand, - Go inside the newly-created target folder, and open the debug folder inside it,
cd target/debug; - You will find NtHiM.exe (on Microsoft Windows) or NtHiM binary (on Linux).
The installation walkthrough for NtHiM has been uploaded to YouTube, covering all of these three methods, and you can watch the video here: How to Install and Use NtHiM (Now, the Host is Mine!)? Super Fast Sub-domain Takeover Detection!
Usage
| Flag | Description | Example |
|---|---|---|
| -h | Display help related to usage! | NtHiM -h |
| -t | Scan a single target! | NtHiM -t https://example.example.com |
| -f | Scan a list of targets from a file! | NtHiM -f hostnames.txt |
| -c | Number of Concurrent Threads! | NtHiM -c 100 -f hostnames.txt |
| -V | Display the version information! | NtHiM -V |
Use Case 1 (Single Target):
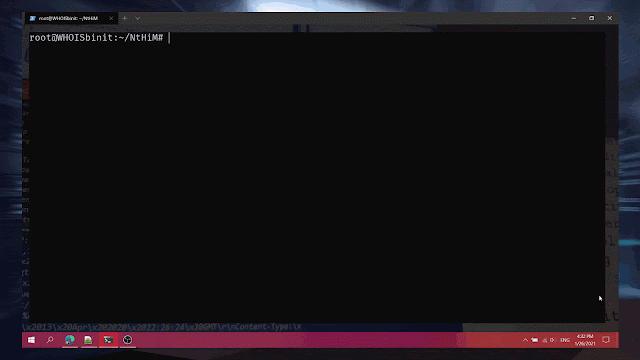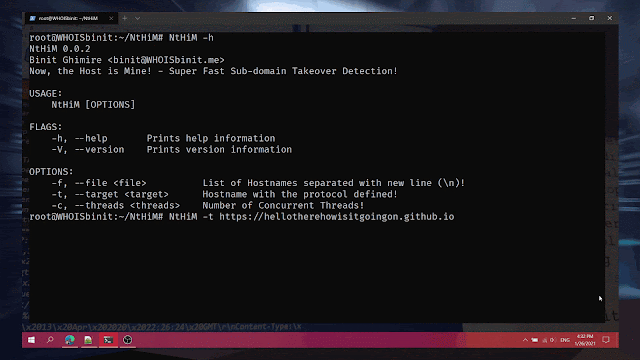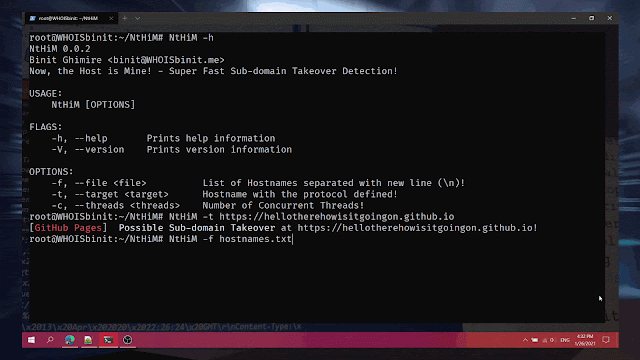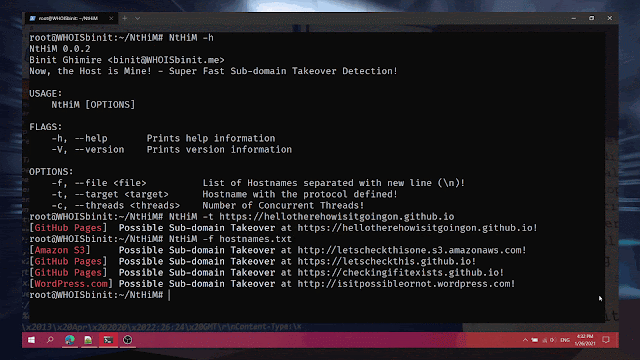
NtHiM -t https://example.example.comUse Case 2 (Multiple Targets):
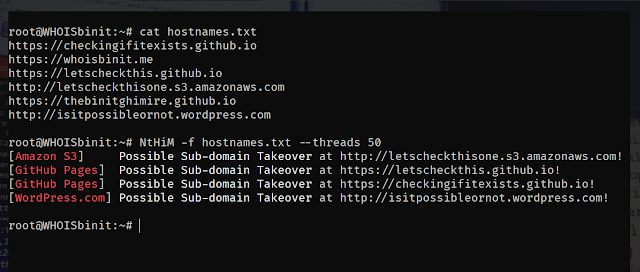
NtHiM -f hostnames.txtUsage Demonstration:
Examples
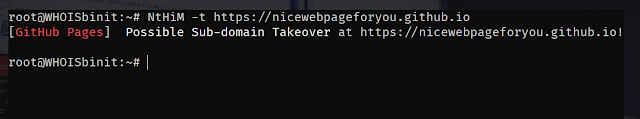
Single Target
Platform Identification
NtHiM uses the data provided in EdOverflow/can-i-take-over-xyz for the platform identification.
Frequently Asked Questions (FAQs)
If you have any questions regarding NtHiM, please raise an issue by going to the Issues page.
Some of your queries might have been answered in one of the existing issues, so please make sure to check the Issues with the FAQ label before raising an issue on your own.
Contributions and Feature Requests
If you are interested in contributing in the development of NtHiM, you can feel free to create a Pull Request with modifications in the original code, or you shall open up a new issue, and I will try to include the feature as requested.
There is no restriction on anyone for contributing to the development of NtHiM. If you would like to contribute, you can feel free to do so.


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren