📚 Pretender - Your MitM Sidekick For Relaying Attacks Featuring DHCPv6 DNS Takeover As Well As mDNS, LLMNR And NetBIOS-NS Spoofing
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: kitploit.com
Your MitM sidekick for relaying attacks featuring DHCPv6 DNS takeover
as well as mDNS, LLMNR and NetBIOS-NS spoofing
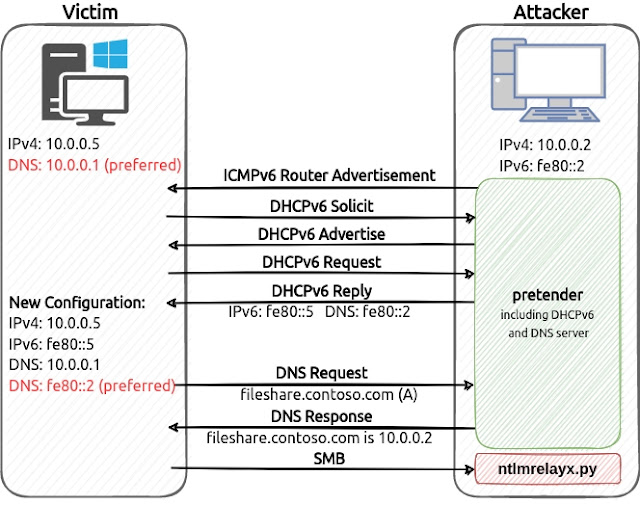
pretender is a tool developed by RedTeam Pentesting to obtain machine-in-the-middle positions via spoofed local name resolution and DHCPv6 DNS takeover attacks. pretender primarily targets Windows hosts, as it is intended to be used for relaying attacks but can be deployed on Linux, Windows and all other platforms Go supports. Name resolution queries can be answered with arbitrary IPs for situations where the relaying tool runs on a different host than pretender. It is designed to work with tools such as Impacket's ntlmrelayx.py and krbrelayx that handle the incoming connections for relaying attacks or hash dumping.
Read our blog post for more information about DHCPv6 DNS takeover, local name resolution spoofing and relay attacks.
Usage
To get a feel for the situation in the local network, pretender can be started in --dry mode where it only logs incoming queries and does not answer any of them:
pretender -i eth0 --dry
pretender -i eth0 --dry --no-ra # without router advertisementsTo perform local name resolution spoofing via mDNS, LLMNR and NetBIOS-NS as well as a DHCPv6 DNS takeover with router advertisements, simply run pretender like this:
pretender -i eth0You can disable certain attacks with --no-dhcp-dns (disabled DHCPv6, DNS and router advertisements), --no-lnr (disabled mDNS, LLMNR and NetBIOS-NS), --no-mdns, --no-llmnr, --no-netbios and --no-ra.
If ntlmrelayx.py runs on a different host (say 10.0.0.10/fe80::5), run pretender like this:
pretender -i eth0 -4 10.0.0.10 -6 fe80::5Pretender can be setup to only respond to queries for certain domains (or all but certain domains) and it can perform the spoofing attacks only for certain hosts (or all but certain hosts). Referencing hosts by hostname relies on the name resolution of the host that runs pretender. See the following example:
pretender -i eth0 --spoof example.com --dont-spoof-for 10.0.0.3,host1.corp,fe80::f --ignore-nofqdnFor more information, run pretender --help.
Tips
- Make sure to enable IPv6 support in
ntlmrelayx.pywith the-6flag - Pretender can be configured to stop after a certain time period for situations where it cannot be aborted manually (
--stop-afterandmain.vendorStopAfter) - Host info lookup (which relies on the ARP table, IP neighbours and reverse lookups) can be disabled with
--no-host-infoormain.vendorNoHostInfo - If you are not sure which interface to choose (especially on Windows), list all interfaces with names and addresses using
--interfaces - If you want to exclude hosts from local name resolution spoofing, make sure to also exclude their IPv6 addresses or use
--no-ipv6-lnr/main.vendorNoIPv6LNR - DHCPv6 messages usually contain a FQDN option (which can also sometimes contain a hostname which is not a FQDN). This option is used to filter out messages by hostname (
--spoof-for/--dont-spoof-for). You can decide what to do with DHCPv6 messages without FQDN option by setting or omitting--ignore-nofqdn - Depending on the build configuration, either the operating system resolver (
CGO_ENABLED=1) or a Go implementation (CGO_ENABLED=0) is used. This can be important for host info collection because the OS resolver may support local name resolution and the Go implementation does not, unless a stub resolver is used. - The host info functionality is currently only available for Windows and Linux.
- A custom MAC address vendor list can be compiled into the binary by replacing the default list
hostinfo/mac-vendors.txt. Only lines with MAC prefixes in the following format are recognized:FF:FF:FF<tab>VendorID<tab>Vendor(the MAC prefix length can be arbitrary). - If you only want to perform Kerberos relaying you can specify
--no-lnrand--spoof-types SOAto ignore any queries that are unrelated to the attack. - When conducting a Kerberos relay attack where
krbrelayx.pyruns on a different host than pretender (relay IPv4 address points to different host that runskrbrelayx.py), the host runningkrbrelayx.pywill also need to run pretender in order to receive and deny the Dynamic Update query sent to the relay IPv4 address.
Building and Vendoring
Pretender can be build as follows:
go buildPretender can also be compiled with pre-configured settings. For this, the ldflags have to be modified like this:
-ldflags '-X main.vendorInterface=eth1'For example, Pretender can be built for Windows with a specific default interface, without colored output and with a relay IPv4 address configured:
GOOS=windows go build -trimpath -ldflags '-X "main.vendorInterface=Ethernet 2" -X main.vendorNoColor=true -X main.vendorRelayIPv4=10.0.0.10'
Full list of vendoring options (see defaults.go or pretender --help for detailed information):
vendorInterface
vendorRelayIPv4
vendorRelayIPv6
vendorSOAHostname
vendorNoDHCPv6DNSTakeover
vendorNoDHCPv6
vendorNoDNS
vendorNoMDNS
vendorNoNetBIOS
vendorNoLLMNR
vendorNoLocalNameResolution
vendorNoRA
vendorNoIPv6LNR
vendorSpoof
vendorDontSpoof
vendorSpoofFor
vendorDontSpoofFor
vendorSpoofTypes
vendorIgnoreDHCPv6NoFQDN
vendorDryMode
vendorTTL
vendorLeaseLifetime
vendorRARouterLifetime
vendorRAPeriod
vendorStopAfter
vendorVerbose
vendorNoColor
vendorNoTimestamps
vendorLogFileName
vendorNoHostInfo
vendorHideIgnored
vendorRedirectStderr
vendorListInterfaces
...


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren