📚 BED -- Bruteforce Exploit Detector
💡 Newskategorie: Hacking
🔗 Quelle: kalilinux.in
In our previous article we discussed about "what is fuzzing ?" In our this article we are going to try a fuzzer (tool for fuzzing).
BED is a plain-text protocol fuzzer which stands for Bruteforce Exploit Detector. Bed checks software for common vulnerabilities like buffer overflows, format string bugs, integer overflows, etc.
It automatically tests the implementation of a chosen protocol by sending different combinations of commands with problematic strings to confuse the target. The protocols supported by this tool are: finger, ftp, http, imap, irc, lpd, pjl, pop, smtp, socks4 and socks5.
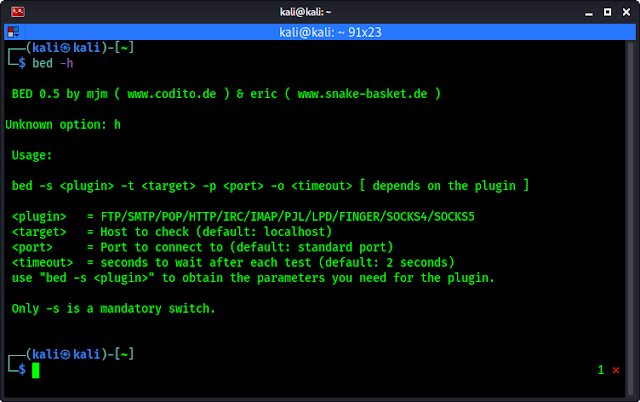
BED comes pre-installed with our Kali Linux system. It is too easy to use so our article will be brief. So lets start:As we mentioned BED comes pre-installed with Kali Linux so check with the help of BED. To do so we need to run following command on our terminal:
bed -hAfter that we can see the help of BED tool, as we can see on the screenshot below.
In the help section (above screenshot) we clearly can see the basic use example of BED. We need to use -s flag to scan, then we need to choose <plugin>, then we need to specify our target (IP address) by using -t flag, then we need to specify our port using -p flag, at last we need to set our timeout by using -o flag.
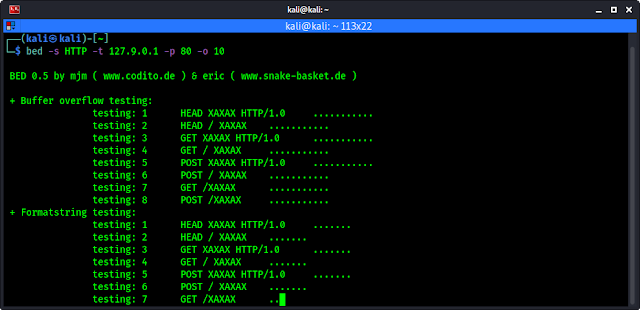
Let's see an example of this, we have an localhost http server on port 80 we try to find vulnerabilities on it by using BED. So our command will be as following:
bed -s HTTP -t 127.9.0.1 -p 80 -o 10The above command will start testing for vulnerabilities on our target (127.9.0.1) as we can see in the following screenshot:
If it got any vulnerability then it will show us by showing errors.
This is how we can use BED fuzzer on our Kali Linux system. Here we need to find IP address of our target.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxInfamily, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren