📚 Monitor Your Cloud Environment with AWS Trusted Advisor ☁️
💡 Newskategorie: Programmierung
🔗 Quelle: dev.to
Cloud security monitoring and increasing visibility are two main important things in the cloud. It helps us to build automated solutions for identifying risky or malicious behavior in the cloud environment. It is also required for every major regulation such as HIPAA, PCI DSS, etc.
Every day there are lots of AWS services that we’re using and gaining visibility and creating monitoring solutions are our responsibility. As your cloud environment grows, there could be many security problems if you don’t know where they are and whether are they configured properly from a security perspective. In AWS, there are lots of security services, and using and managing them is our responsibility. One of them is AWS Trusted Advisor a service that analyzes your AWS environment and provides recommendations for you in five categories: Cost optimization, security, fault tolerance, performance, and service limits.
In this blog, we’re focusing on the security part of the AWS Trusted Advisor. But you should consider the other parts of improving your environment such as cost, performance, etc.
In the AWS Trusted Advisor, there are lots of controls for security configurations of your AWS resources, some examples are the following:
Security Groups — Specific Ports Unrestricted: This control checks security groups for rules that allow unrestricted access to specific ports such as SSH and RDP. Unrestricted access increases opportunities for malicious activity (hacking, denial-of-service attacks, loss of data).
Amazon RDS Public Snapshots: This control checks the permission settings for your Amazon RDS DB snapshots and alerts you if any snapshots are marked as public. When you make a snapshot public, you give all AWS accounts and anonymous users access to all the data on the snapshot. If sharing snapshots is a requirement for you, you can mark the snapshot as private and then specify the user or accounts you want to share.
In AWS Trusted advisor, some security controls are enabled by default and free, and some of them are needs upgrading your AWS Account and you need to pay for it. These controls are more deep-dive solutions and recommendations for you.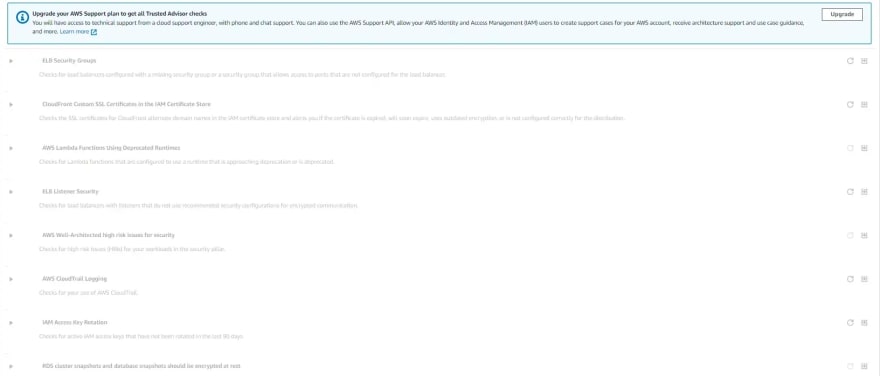
Automated Monitoring of Trusted Advisor Security Checks:
From a cloud security perspective, enabling AWS Trusted Advisor is not enough. We need to automate and get action about controls. But AWS Trusted Advisor scenarios are different plan by plan. You can use the Trusted Advisor console to access checks in the security category if you have a Basic/Developer Support plan. If you have other plans, in addition to all of these, you can use AWS Support API to access all Trusted Advisor checks. You can also Amazon CloudWatch or EventBridge events to monitor and alarm.
Using Trusted Advisor with Different Scenarios:
1) You have a strict security policy for your databases. You do not want publicly accessible snapshots in your test and production environment. Also, you should not configure the security group rule of your databases overly permissive. If these actions are taken, there should be an incident response plan, to roll back all these configurations.
Solution: You can use AWS Trusted API metrics for this incident response plan. You can set an Amazon EventBridge Rule for these checks:
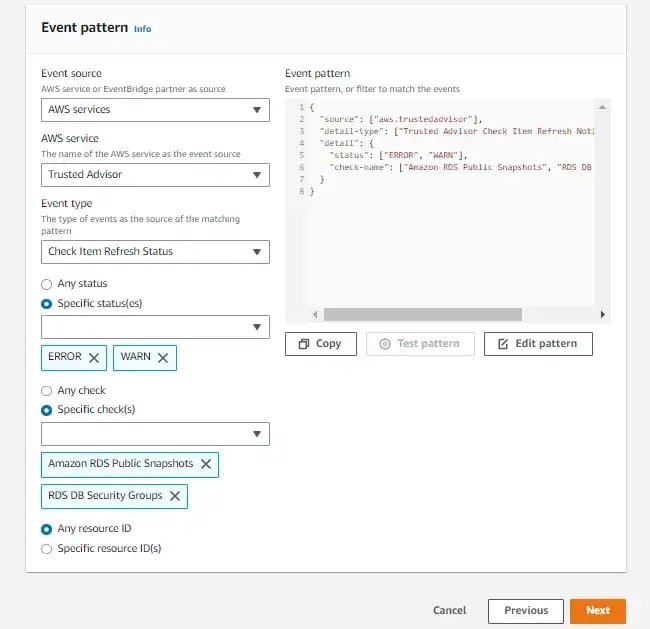
When this rule is triggered, you can invoke an AWS Lambda function that rolls back all the changes such as deleting overly permissive rules in the security group and disabling publicly accessible snapshots. You can use AWS SDK functions for these. This is the architectural design:
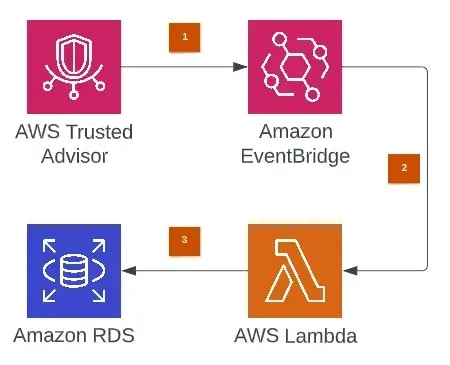
Note: You need to upgrade your support plan for this. The Basic Plan which is enabled when you create a new account does not support AWS Trusted Advisor metrics. You have only a console view in this plan.
2) Your security team wants to get a weekly summary security report of your environment. Do you need a custom solution or AWS Trusted Advisor can do that?
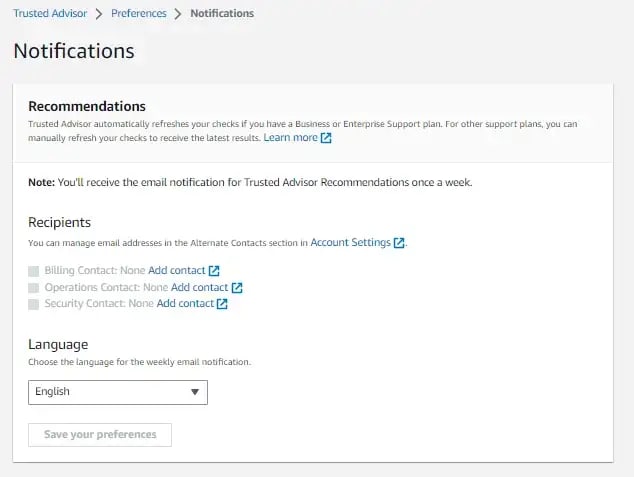
Solution: In the Trusted Advisor, there is a “Notification” solution. You can receive the email notification for Trusted Advisor Recommendations once a week. You need to add your security, billing and operations contact e-mail addresses. You can also set up a Slack solution with this.
There are some useful links that I want to share with you if you want to implement them:
Trusted Advisor with AWS Organizations: AWS Premium Support customers can use Trusted Advisor from an Organizational View. This provides a general and centralized view of all AWS Trusted Advisor recommendations.
Trusted Advisor Tools: This is a perfect GitHub repo for automating Trusted Advisor checks with AWS CloudFormation templates.
Trusted Advisor Best Practices: There are some best practice rules for AWS Trusted Advisor by TrendMicro.
Thanks for reading! Stay safe in the cloud! 🤞 ⛅️
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren