📚 AWS VPC BASICS
💡 Newskategorie: Programmierung
🔗 Quelle: dev.to
What is AWS VPC ?
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud. You can specify an IP address range for the VPC, add subnets, add gateways, and associate security groups.
What are the components of AWS VPC ?
Components of AWS VPC
- Route Table: In AWS Virtual Private Cloud, route Tables are the set of rules, that are used to determine where the network traffic has to be directed. The route table specifies the destination (IP address) and target (where do want to send the traffic to that destination). The target can be an Internet gateway, NAT gateway, Virtual private gateway, VPC peering connection, etc
In the diagram below, we've added two route tables: the main route table and the custom route table. The new route table or the custom route table informs the internet gateway to direct
internet traffic to the public subnet. However, the private subnet is still associated with the default route table, the main route table that does not allow internet traffic. All traffic inside the private subnet remains local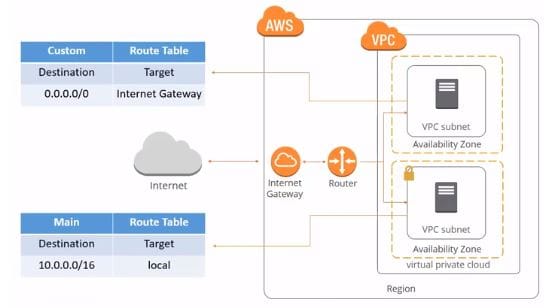
- Subnet: It is a portion of the network that shares a common address component. All devices whose addresses have the same prefix are in the same subnet. For example, all those devices whose IP address would start with 172.31.1 would be part of the same subnet. There are two types of subnets. Private Subnet where resources are not exposed to the outside world and Public Subnet where resources are exposed to the internet through Internet Gateway.
- Security Groups: Security groups are a set of firewall rules that controls the traffic for your instance. In Amazon Firewall the only action that can be carried out is allowed. You cannot create a rule to deny. The destination is always the instance on which the service security group is running. You can have a single security group associated with multiple instances.
- Internet Gateway An internet gateway (IGW) is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet. It supports IPv4 and IPv6 traffic. It does not cause availability risks or bandwidth constraints on your network traffic.
- NAT Gateway: Network Address Translation (NAT) Gateway is used when higher bandwidth and availability with lesser administrative effort is required. NAT gateway always resides inside the public subnet of an Availability Zone. It updates the routing table of the private subnet such that it sends the traffic to the NAT gateway. Elastic IP must be attached to the NAT gateway while creating. It supports only TCP, UDP, and ICMP protocols.
- VPC Peering: A VPC peering connection allows you to route traffic between two Virtual Private Cloud’s using IPv4 or IPv6 private addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. A VPC peering connection helps you to facilitate the transfer of data
- Network Access Control Lists (NACL): Network Access Control Lists is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC. The default network ACL is configured to allow all traffic to flow in and out of the subnets to which it is associated.
- Virtual Private Gateway: A virtual private gateway is the VPN concentrator on the Amazon side of the VPN connection. You create a virtual private gateway and attach it to the VPC from which you want to create the VPN connection.
- Customer Gateway: An Amazon VPC VPN connection links your data center (or network) to your Amazon VPC (virtual private cloud). A customer gateway is an anchor on your side of that connection. It can be a physical or software appliance.
- Elastic IP: Elastic IP is a static IP address that never changes and is a reserved public IP address that can be assigned to any Instance in a particular region. An elastic IP is reserved for your AWS account and is yours until you release it.
- Network Interface: Network Interface is a point of connection between a public and a private network. Every instance has a default network interface, called the primary network interface. Network traffic is automatically shifted to the new instance if you move it from one instance to the other.
- VPC Endpoints: VPC endpoints allow private connection between your AWS VPC and other AWS services without using the internet. VPC endpoint devices are scaled, redundant, and highly available VPC components. There are two types of AWS Virtual Private Cloud endpoints Interface endpoints and Gateway Endpoints.
- VPC direct connect: AWS Direct Connect is a networking service that provides an alternative to using the internet to connect to AWS. Using AWS Direct Connect, data that would have previously been transported over the internet is delivered through a private network connection between your facilities and AWS.
VPC Limitations
- Five VPCs per region
- 200 subnets per VPC
- 200 route tables per VPC
- 500 security groups per VPC
- 50 inbound and outbound rules per VPC
NB: some of the above limits can be increased by submitting a ticket to AWS support.
REFERENCE:
- https://docs.aws.amazon.com/vpc/index.html
- https://k21academy.com/amazon-web-services/aws-vpc-virtual-private-cloud/
- https://aws.plainenglish.io/aws-vpc-refresher-40ac90196ea8
- https://www.simplilearn.com/tutorials/aws-tutorial/aws-vpc
- https://docs.aws.amazon.com/whitepapers/latest/aws-vpc-connectivity-options/aws-direct-connect.html


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren