📚 Exploit Code Released for Actively Exploited GoAnywhere MFT Vulnerability
💡 Newskategorie: Hacking
🔗 Quelle: blackhatethicalhacking.com
Exploit Code Released for Actively Exploited GoAnywhere MFT Vulnerability
Reading Time: 3 Minutes
Actively exploited zero-day vulnerability on GoAnywhere MFT
An actively exploited zero-day vulnerability affecting Internet-exposed GoAnywhere MFT (Managed File Transfer) administrator consoles has been made public by security researcher Florian Hauser of IT security consulting firm Code White.
Well done @frycos, such a sweet pre-auth RCE! https://t.co/JRE9DcXOGb pic.twitter.com/cJlvEmL2Km
— ϻг_ϻε (@stevenseeley@infosec.exchange) (@steventseeley) February 4, 2023
GoAnywhere MFT is a web-based tool designed to help organizations securely transfer files and keep audit logs of access. The vulnerability allows for unauthenticated remote code execution on vulnerable GoAnywhere MFT servers.
Although Fortra (the developer behind GoAnywhere MFT) claims that the attack vector requires access to the administrative console of the application, which is usually accessible only from within a private network, Shodan scan results show that almost 1,000 GoAnywhere instances are exposed on the Internet.
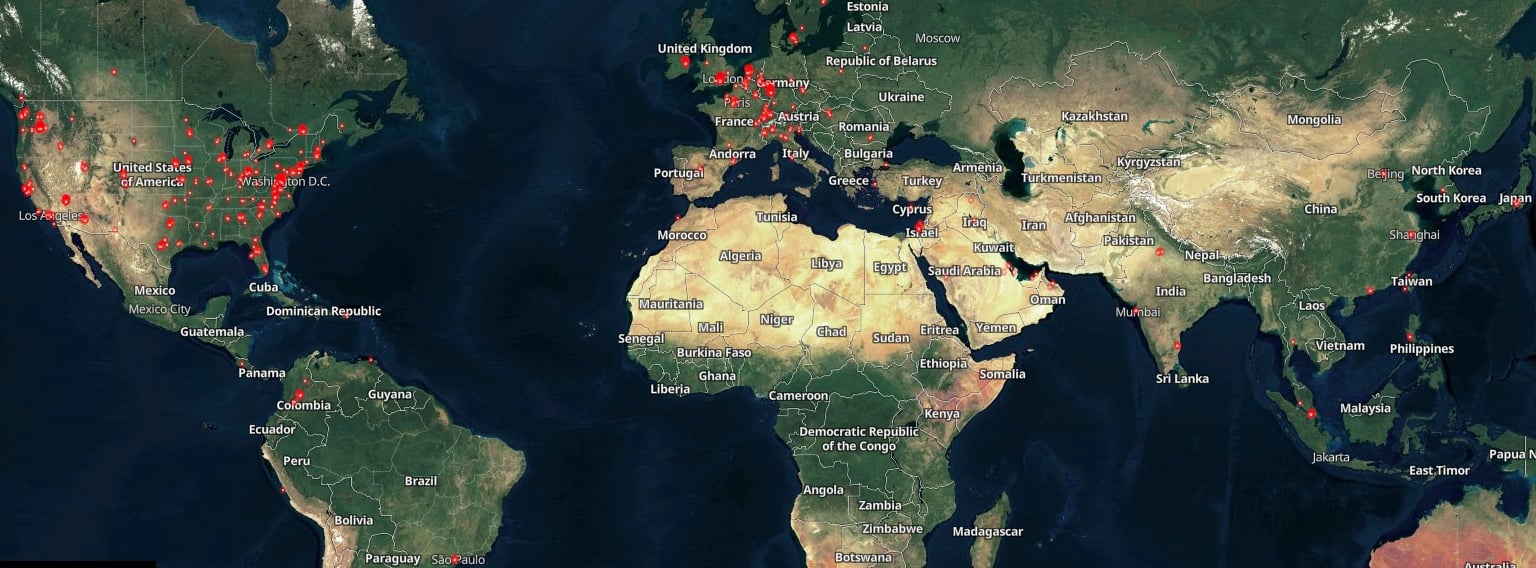 Map of vulnerable GoAnywhere MFT servers (Shodan)
Map of vulnerable GoAnywhere MFT servers (Shodan)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Fortra has not yet acknowledged the vulnerability
Fortra has yet to publicly acknowledge the security flaw and has not released any security updates to address the vulnerability, leaving all exposed installations vulnerable to attacks. The company has provided indicators of compromise, including a specific stacktrace that shows up in the logs on compromised systems.
Trending: Major Cyber Attacks of 2022
Trending: Recon Tool: ScopeHunter
Mitigation
To mitigate the vulnerability, Fortra recommends implementing access controls to allow access to the administrative interface only from trusted sources, disabling the licensing service, revoking stored credentials for other systems, rotating the Master Encryption Key, resetting credentials for all external trading partners/systems, reviewing audit logs and deleting any suspicious admin and/or web user accounts.
The company advises users to contact support via their portal, email or phone for further assistance.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren





