📚 AWS Networking - AWS VPC, Subnets, Security Groups, NAT Gateway & IP Addresses
💡 Newskategorie: Programmierung
🔗 Quelle: dev.to
AWS Networking can be a complicated topic, but it's an essential part of building and managing resources on the AWS Cloud. In this comprehensive guide, we'll take a deep dive into the key components of AWS Networking and explore everything you need to know to get started.
let the game begins...
Virtual Private Clouds (VPCs)
At the heart of AWS Networking is the Virtual Private Cloud (VPC). A VPC is a virtual network that enables you to launch AWS resources into a virtual network that you define.It provides you with complete control over your virtual networking environment, including the selection of IP address ranges, subnets, and configuration of route tables and network gateways.
Let's look at each of these component in detail.
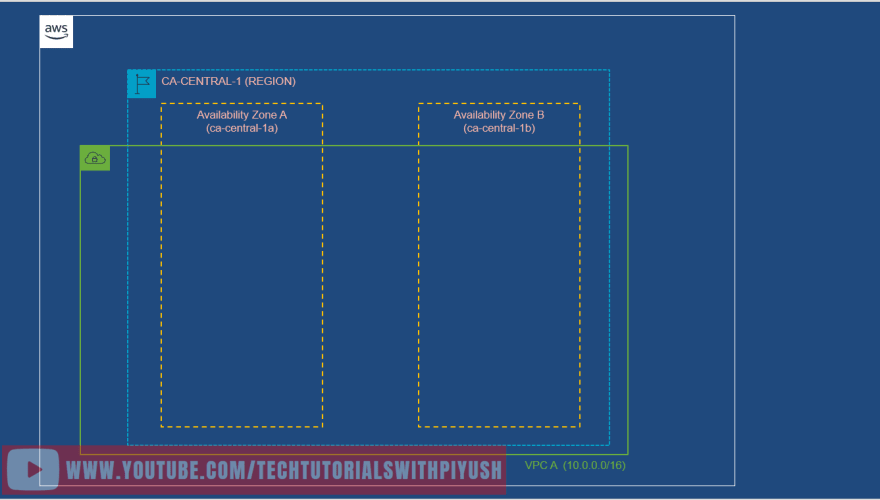
- Resources that you create in AWS resides pysically in one or more Data Centres usually 100 miles apart from each other.
- Collection of multiple data centres are referred to as an Availability Zone such as ca-central-1a , ca-central1b.
- Collection of multiple Availability zones in a geographical location is referred to as an *AWS Region such as ca-central-1.
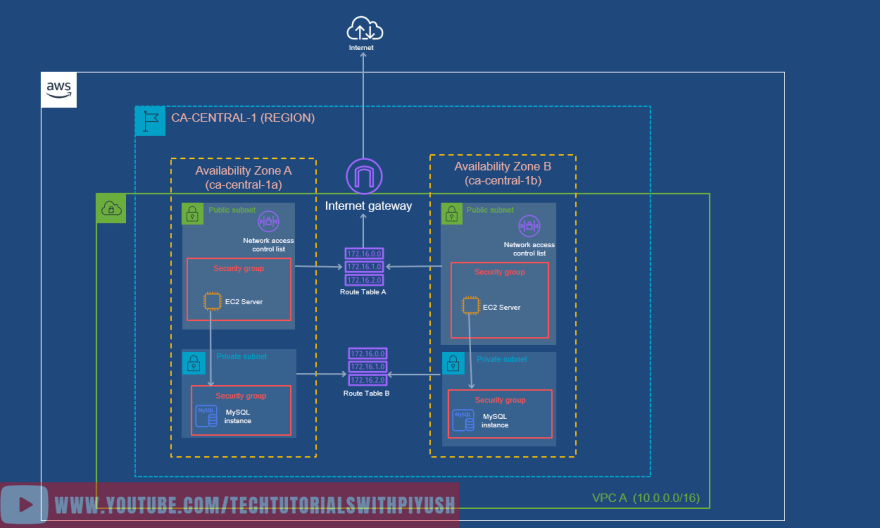
Below diagram shows an AWS Region(ca-central-1) that consists of two Availability Zones (ca-central-1a and ca-central-1b) that are part of VPC A with the CIDR range(10.0.0.0/16)
Subnets
A subnetwork or subnet is a logical subdivision of an IP network.
It further divides a VPC into multiple small networks so that they can be managed seperately.
The practice of dividing a network into two or more networks is called subnetting.
For example, a VPC having 10.0.0.0/16 = 65,536 IPs can be broken down into 4 subnets:
- 10.0.1.0/24 = 256 IPs
- 10.0.2.0/24 = 256 IPs
- 10.0.3.0/24 = 256 IPs
- 10.0.4.0/24 = 256 IPs
5 IPs per CIDR are reserved by AWS and rest of them will be available for further use.
Types of Subnets:
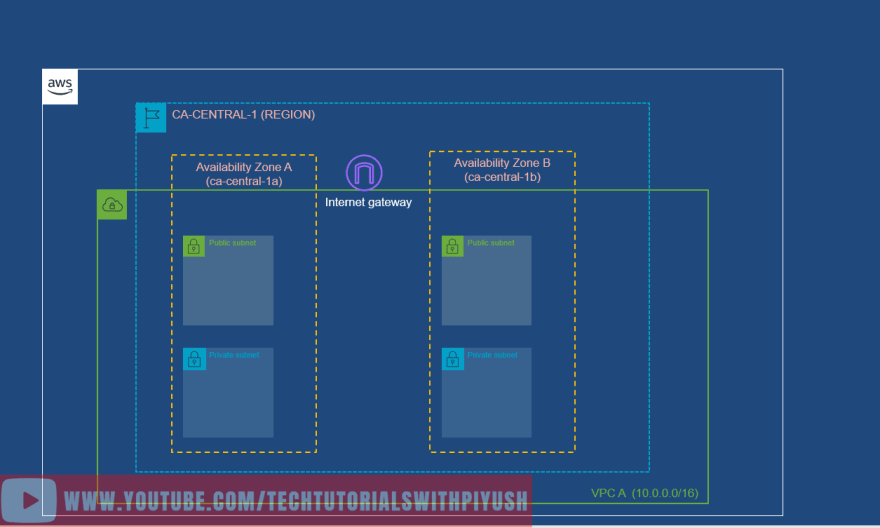
There are two types of subnets: Private and Public.
Public Subnets: If you want your instance in a public subnet to communicate with the internet then you use public subnet. Generally, web facing instances are placed in Public subnets.
Private Subnet: If a subnet doesn't have a route to the internet gateway, the subnet is known as a private subnet.
Generally, your DB servers are places in private subnets.
In the below diagram, we have added 1 Public and 1 Private subnet in each of the Availability zones.
Internet Gateway
Internet Gateway allows communication between your VPC and the internet. Only one IGW can be attached to one VPC and vice-versa.
In the below diagram, we have attached Internet Gateway to the VPC.
Internet gateway itself doesn’t provide access to the internet
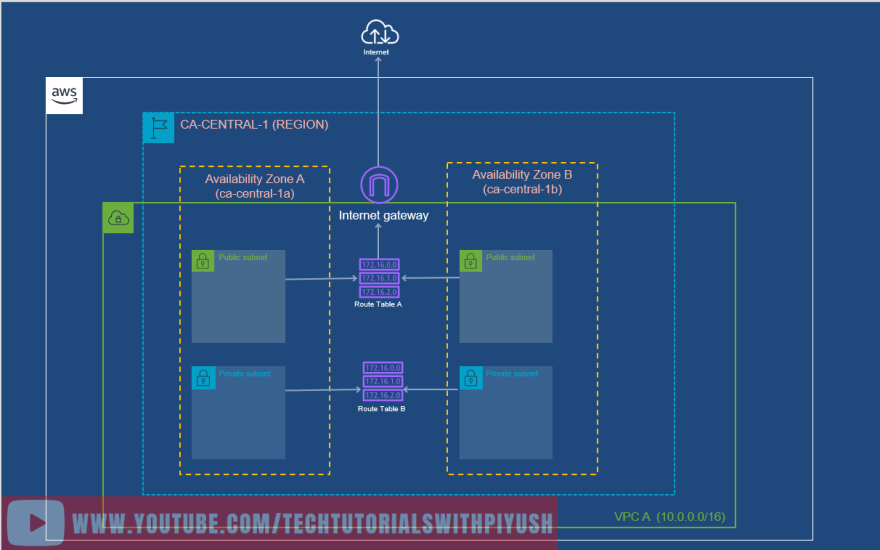
Route table must be associated with the subnets and routes should be defined.
A route table contains a set of rules, called routes, that are used to determine where network traffic from your subnet or gateway is directed.
Public Subnet should have a route to the internet gateway while , Private subnet should have a route to the local network. As shown in the below diagram:
After attaching the route tables with the subnets, our diagram will look something like below
Now, lets talk about another important feature of VPC:
Security Groups
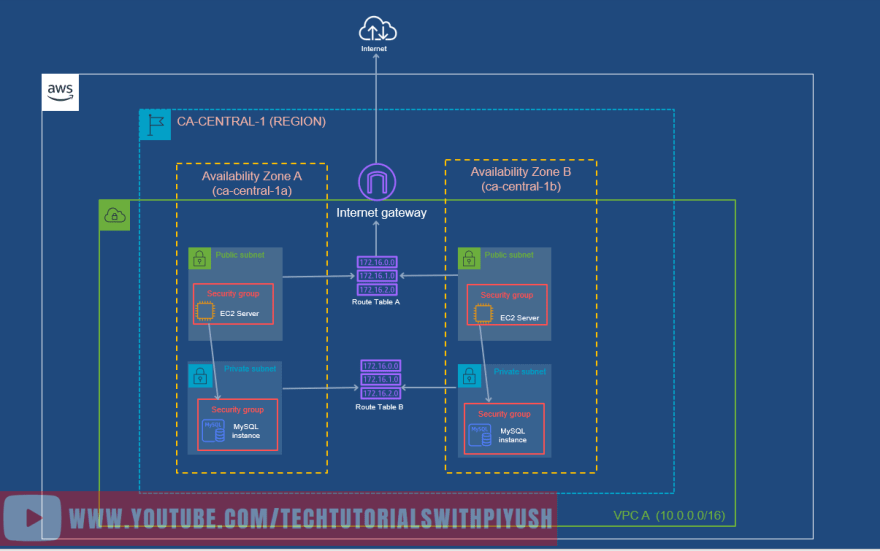
- A security group acts as a virtual firewall for your EC2 instances to control incoming and outgoing traffic.
- Inbound rules control the incoming traffic to your instance, and outbound rules control the outgoing traffic from your instance.
- In the rules, you define, what type of traffic is allowed/denied from which source. e.g allow http traffic from 0.0.0.0 to the EC2.
Once you attach these security groups with your EC2 instances, the diagram will look something like below:
NACL(Network Access Control List) :
Like Security groups acts as a firewall on EC2/host level, NACL or Network Access control list acts as an additional layer of firewall on subnet level.
Default NACL allows all inbound and outbound traffic to your subnets.You can create a custom network ACL and associate it with a subnet.
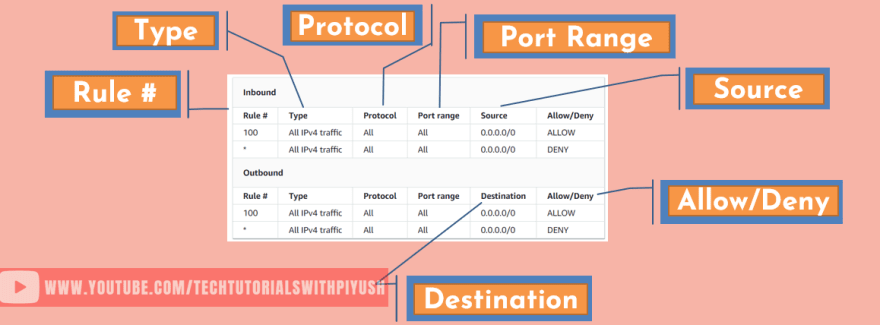
A network ACL contains rules and a priority assigned to each rule, rules are evaluated based
on their priority, lower the number, higher the priority.
Below is a sample NACL Rule:
After adding the NACL rules to your subnets, our diagram will look something like below:
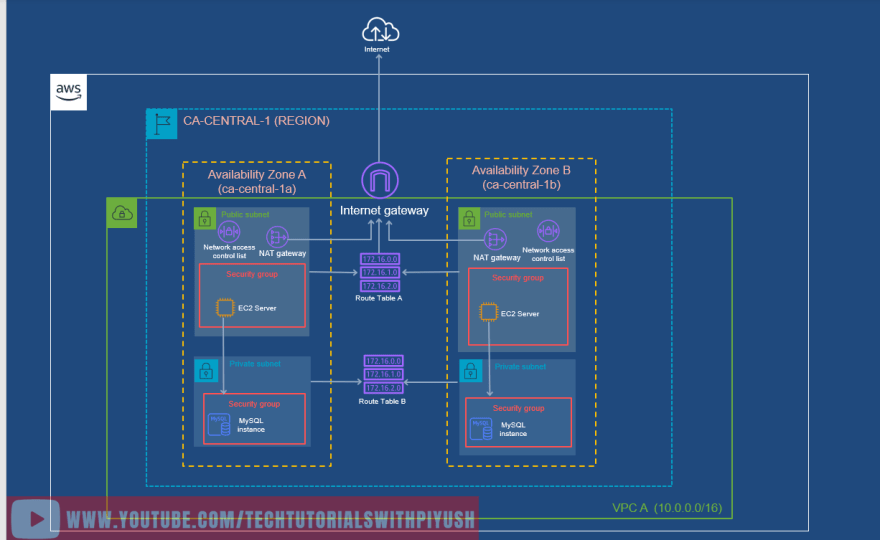
Now, there are a lot of usecases where your instances in private subnet needs access to the internet. For instance, Database instance needs regular updates/patching to be done by downloading updates from the internet. This can be done securely using NAT Gateway which allows instances in the private subnet to connect to the internet via a secure route.
Nat Gateways should be launched in Public Subnets (One per AZ). Something like below:
Conclusion
AWS Networking can be a complicated topic, but by following best practices and using the tools provided by AWS, you can build a secure and efficient network for your resources.
Want to see all the networking components with detailed explanation? Check out the below tutorial for the same:
References 📚:
https://docs.aws.amazon.com/vpc/latest/userguide/amazon-vpc-limits.html
https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-security-groups.html
https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html
https://aws.amazon.com/about-aws/global-infrastructure/
https://docs.aws.amazon.com/vpc/latest/userguide/default-vpc.html
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-instance-addressing.html


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren