📚 TP-Link WN722N V2/3 Monitor Mode & Packet Injection Support
💡 Newskategorie: Hacking
🔗 Quelle: kalilinux.in
TP-Link WN722N is a very popular WiFi adapter for wireless auditing. It is low budget and beginner friendly so cybersecurity students and new learners always look for it. Now it becomes a problem because TP-Link WN722N Version 1 comes with Atheros AR9002U chipset and supports monitor mode and packet injection. Version 2/3 has the Realtek RTL8188EUS chipset and doesn’t support monitor mode or packet injection. Also TP Link N150 TL-WN722N version 1 have low availability in the market right now.
So in our this article we are going to cover how we can set TP-Link WN722N Version 2 or Version 3 on our Kali Linux and for Monitor Mode & Packet Injection. In that way we can use this affordable and reliable WiFi adapter for WiFi security testing.
We got a TP-Link WN722N Version 2 WiFi adapter on our hand (shown in the following picture) and we will show how to use Monitor Mode and Packet Injection on it.
.webp) |
| We can see the Model and Version on the back of the device |
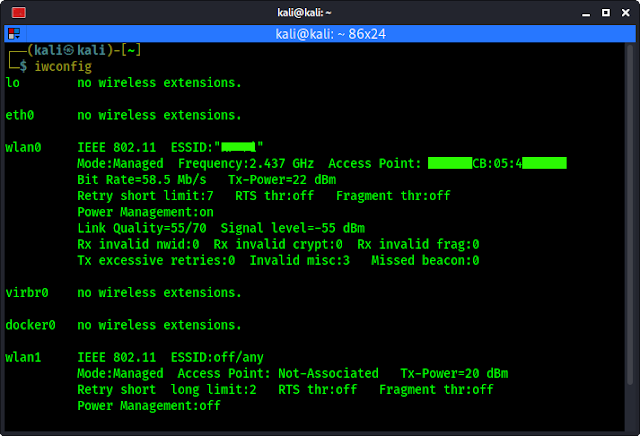
iwconfig
In the above screenshot we can see that in our case wlan0 is our system's inbuilt wireless interface and wlan1 is our TP-Link WN722N's network interface (wlan0 and wlan1 etc depends on the system, confused what is yours? Then unplug the TP-Link WN722N and run ifconfig and check then again plug it in and check again you will get it).
Now we run the following command to check if Packet Injection is supported or not on our TP-Link WN722N WiFi adapter by using following command:
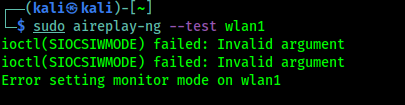
sudo aireplay-ng --test wlan1
The output shown in the following screenshot:
In the above screenshot we can see that our external WiFi adapter don't support Monitor Mode. So, we need to change the driver of this TP-Link WN722N adapter.
TP-Link WN722N V 2/3 Monitor Mode on Kali Linux
First of all we need to have an updated Kali Linux system (sudo apt update && sudo apt upgrade), We are on all updated Kali Linux box. Then we need to install some dependencies on our system by applying following command:
sudo apt install dkms bc build-essential libelf-dev -y
After applying the above command above programs will be installed on our system as we can see in the following screenshot:
Then we need to check for kernel updates by using following command:sudo apt install linux-headers-$(uname -r)
In the following screenshot we can see that we are already on a updated kernel:
Now we remove the current driver of RTL8188EUS driver by using following command:
sudo rmmod r8188eu.ko
Then we need to be the root user by applying following command:
sudo -i
We can see the results of the above commands in the following screenshot:
Now we need to blacklist old drivers by using following commands one by one:
echo "blacklist 8188eu" >> "/etc/modprob.d/realtek.conf"
echo "blacklist r8188eu" >> "/etc/modprob.d/realtek.conf"After it is done our old drivers are removed. Here we need a reboot, rebooting our system will prevent errors for the rest of this setup. So we must need to Reboot.
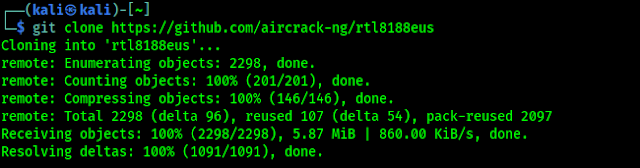
After a reboot we need to install that driver which one supports Monitor Mode & Packet Injection on TP-Link WN722N. To do that we need to clone a driver built by aircrack-ng form GitHub by using following command on our terminal window:
git clone https://github.com/aircrack-ng/rtl8188eus
We can see cloning process on the following screenshot:
After the installation process is done, we need to navigate to our cloned directory by applying following command:cd rtl8188eus
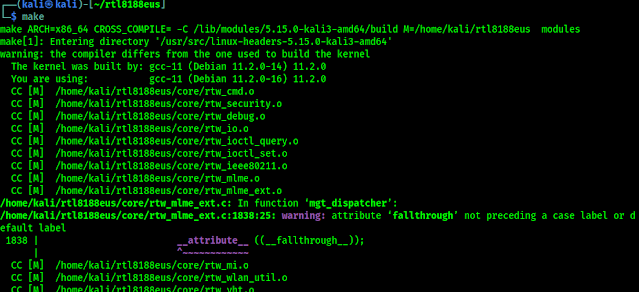
Then we need compile this driver by using following command:
sudo make
Following screenshot shows the output of the compilation process:
This compilation process may take couple of minutes depending on our system performance. Then we need to run following command to install the compiled driver:
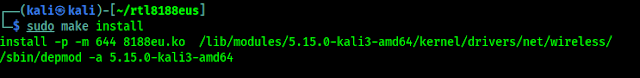
sudo make install
Following screenshot shows the output of the command:
Now we need to run following command to set all up:
sudo modprobe 8188eu
Now we are almost set, we just need a reboot. If everything was right then we are ready to rock after reboot. After the reboot is done let's again check our network interfaces using following command:
iwconfig
Here we can see that the mode is still not showing Monitor Mode. Wait a bit, we need to turn on Monitor Mode on our wlan1 interface. To do that we run following commands on our terminal one by one:
sudo ifconfig wlan1 down
sudo iwconfig wlan1 mode monitor
Now we can check our network interfaces status by using following command:
iwconfig
We can see the output in the following screenshot:
In the above screenshot we can see that our wlan1 got Monitor Mode (highlighted in red). BINGO
Let's check it it is working well or not by scanning WiFi networks around us. To do so we need to run following command:
sudo airodump-ng wlan1
We can see the output on the following screenshot:
In the above screenshot we can see that we can scan for targets with our TP-Link WN722N Version 2 WiFi adapter on our Kali Linux system.
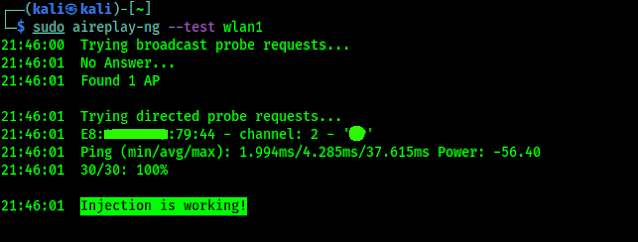
Let we check for packet injection by using following command (We tried this on the beginning):
sudo aireplay-ng --test wlan1
In the following screenshot we can see the output of the applied command:
In the above screenshot we can see that Packet Injection is working" on our TP-Link WN722N Version 2 WiFi adapter on our Kali Linux system.
Video Tutorial
Our article is inspired from David Bombal's Youtube video. We can check his following video for a video tutorial:
This is how we can get monitor mode and packet injection support on TP-Link WN722N version 2 and 3 (same process) on our Kali Linux system.Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren