📚 Kelihos Analysis - Part 1
💡 Newskategorie: Video
🔗 Quelle: malwaretech.com
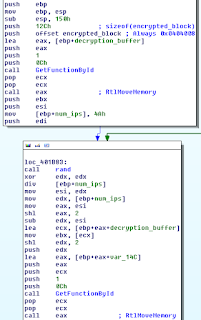
Surprisingly I've never even looked at Kelihos before as it's been around way longer than I've been reverse engineering, and every time I heard about it during my reversing days it was because it had been taken down...again. Well, last month a friend of mine was talking about how Kelihos was spreading again via Nuclear exploit kit, prompting me to contact the exploit pack guru @Kafeine, and request a recent sample.
Something interesting to note is that Kelihos spreads aggressively via exploit kits, rather than growing slowly over time through self propagation. This is why the many takedown attempts have had little effect as the botmaster can simple sets up new infrastructure and starts spreading again within a few a couple of days (Researchers had reported a new sample being spread less 24 hours after the most recent takedown).


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren