📚 Bootkit Disk Forensics - Part 2
💡 Newskategorie: Video
🔗 Quelle: malwaretech.com
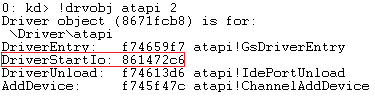
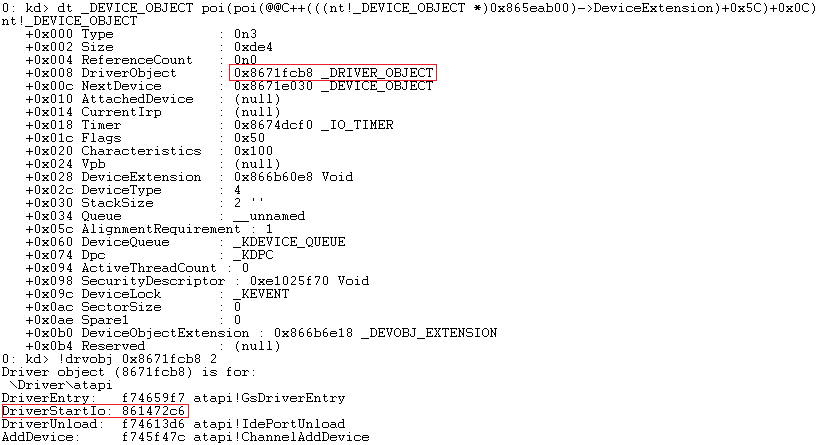
DriverStartIo
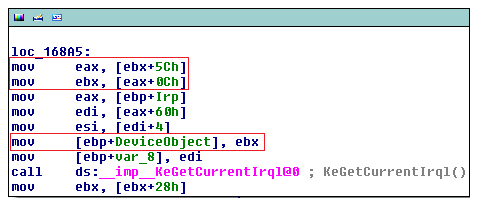 |
| To start with, ebx is the address of the device extension (which is shared between all atapi devices). |
The call logic is something like this:
- Get the miniport's device extension from its device object (passed to us in the call).
- Get IdePort1's device extension from offset 0x5C into the miniport's device extension.
- Get IdePort1's device object from offset 0x0C into its device extension.
- Call IoStartPacket with the IRP and IdePort1's device object.
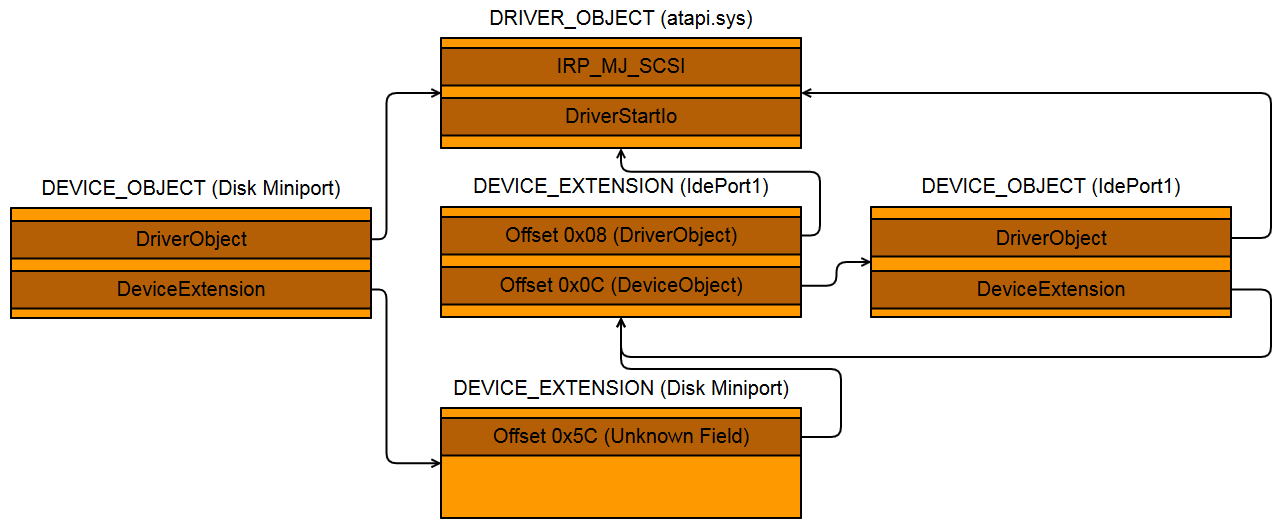 |
| The relationship between the various objects. |
Detecting DriverStartIo hook with WinDbg
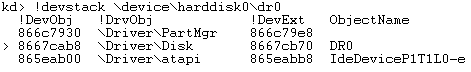 |
| Device stack for boot device on a clean system |
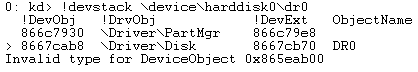 |
| Device stack on a TDL4 infected system. |
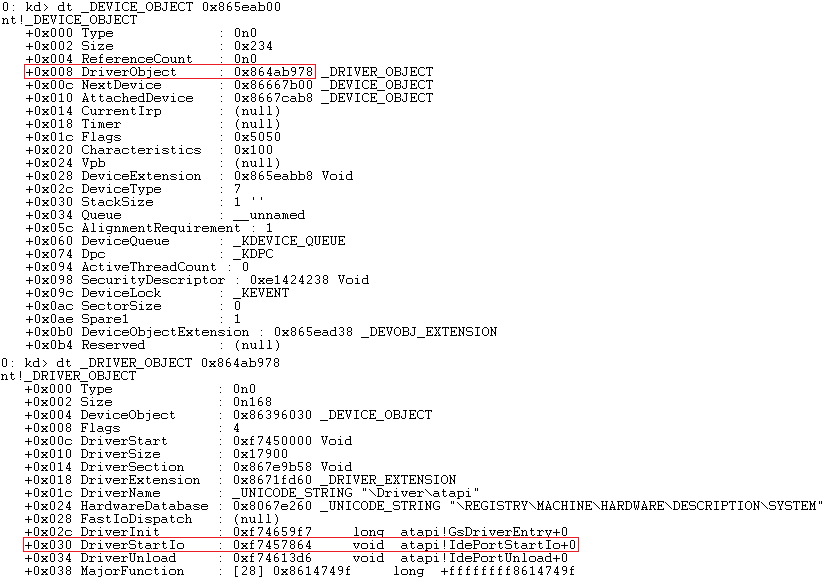 |
| DriverStartIo appears not to be hooked. |
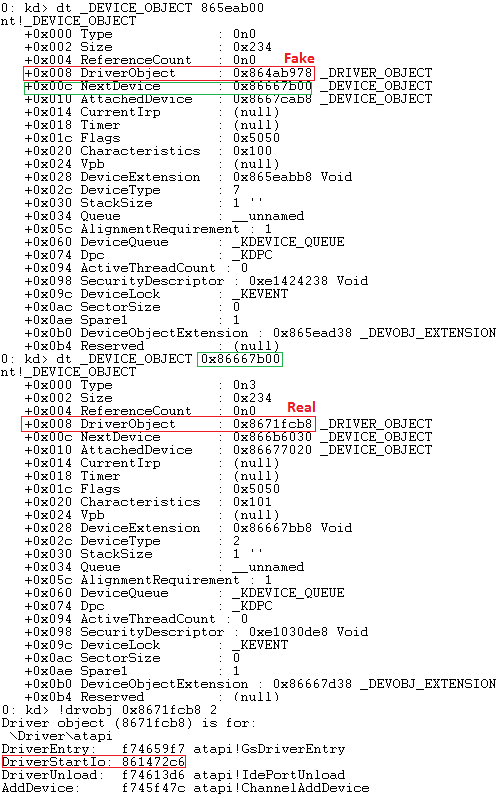 |
| All devices should point to the real driver object, except for the miniport. |
Method 3: DeviceExtension


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren