📚 Bootkit Disk Forensics - Part 3
💡 Newskategorie: Video
🔗 Quelle: malwaretech.com
Getting Original Pointers
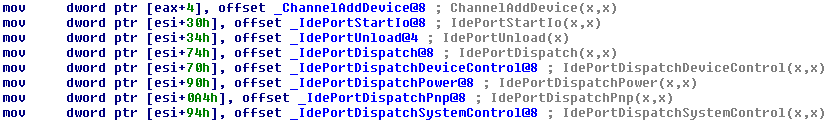 |
| An example of code initializing the driver object (taken from atapi.sys) |
The obvious problem with this method is the initialization code may not be in DriverEntry, but a sub function called from it (it may even be necessary to follow jumps). It's also not guaranteed that the instruction will use esi as the pointer to the driver object or an immediate for the function address, in fact you're probably going to have to account for quite a few different instructions.
Bypassing Inline Hooks
Usually a hook is placed within the first few bytes of a function, so you can simply read and relocate the first few bytes from the clean function into a buffer, then append it with a jump to the same offset within the real driver(this is the same way a hooking engine would call the unhooked version of a function).
Creating a Clean Call Path
- Get the device object for the boot disk miniport, this is usually \Device\Harddisk0\Dr0
- Use the size field of the device object to allocate some non paged memory and copy the entire object (this is your clean miniport).
- Set the DriverObject field to point to your own driver's object, in which you've set the IRP_MJ_SCSI and DriverStartIo field appropriately (DriverStartIo can be skipped on Vista+).
- Set the DeviceExtension field of your clean miniport device object to point to directly after its device object (DeviceObject + sizeof(DEVICE_OBJECT)).
- Get the address stored at offset 0x5C into your clean miniport's device extension and check it's valid (this is the address of the corresponding port's device extension).
- Read the addresses stored at offset 0x0C into the port's device extension (this is the address of the port's device object).
- Use the size field of the port's device object to allocate some non paged memory and copy the entire object (this is your clean port).
- Set the DeviceExtension field of your clean port's device object to point to directly after its device object (DeviceObject + sizeof(DEVICE_OBJECT)).
- Set the DriverObject field of your clean port's device object to point to your own driver's object, in which you've set the IRP_MJ_SCSI field appropriately.
- Change offset 0x5C into your clean miniport's device extension to contain the address of the clean port's device extension.
- Set offset 0x0C into the clean port's device extension to contain the address of the clean port's device object.


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren