📚 Pwn2Own Returns to Vancouver for 2020
💡 Newskategorie: Hacking
🔗 Quelle: thezdi.com
As each new year starts, we at the Zero Day Initiative begin to think of spring and the Vancouver edition of the Pwn2Own contest. It was in Vancouver where the contest began back in 2007 and continues to be where we push the research community and ourselves with new challenges. What do we want to see demonstrated? What products should we focus on? Last year, we raised more than a few eyebrows by partnering with Tesla to include a Model 3, the best-selling car in its class in the U.S., as a target, and we ended up awarding the car to two talented researchers. We wanted to include Tesla because they pioneered the concept of a connected car and over-the-air updates nearly a decade ago, and they have been leading the space ever since.
This year, Tesla returns to the contest. Driving off with a brand-new Model 3 will be a harder challenge this year, which means the potential rewards will be much higher as well. Microsoft also returns as partner and VMware returns as a sponsor with their somewhat more traditional Pwn2Own targets. All told, more than $1,000,000 USD in cash and prizes are available to contestants, including the new Tesla car.
As usual, we will hold Pwn2Own at the CanSecWest conference, which occurs on March 18-20 of this year. Here’s a complete look at all six of the categories available for this contest:
-- Automotive Category
-- Web Browser Category
-- Virtualization Category
-- Enterprise Applications Category
-- Server-Side Category
-- Local Escalation of Privilege Category
And, of course, Pwn2Own would not be complete without us crowning a Master of Pwn. Since the order of the contest is decided by a random draw, contestants with an unlucky draw could still demonstrate fantastic research but receive less money since subsequent rounds go down in value. However, the points awarded for each successful entry do not go down. Someone could have a bad draw and still accumulate the most points. The person or team with the most points at the end of the contest will be crowned Master of Pwn, receive 65,000 ZDI reward points (instant Platinum status), a killer trophy, and a pretty snazzy jacket to boot.
Let’s take a look at the details of the rules for this year’s contest.
Automotive Category: Tesla Model 3
Last year was the first year for the Automotive category, and we’re excited to have Tesla return as partner for 2020. However, we wanted to up the level of complexity for this year’s event. Tesla vehicles are equipped with multiple layers of security, and this time around, there are three different tiers of awards within the Automotive category that correspond to some of the different layers of security within a Tesla car, with additional prize options available in certain instances.
Tier 1 earns the top prizes and represents a complete vehicle compromise. Correspondingly, this also has the highest award amounts. To win this level, a contestant will need to pivot through multiple systems in the car, meaning they will need a complex exploit chain to get arbitrary code execution on three different sub-systems in the vehicle. Success here gets a big payout and, of course, a brand-new Tesla Model 3.
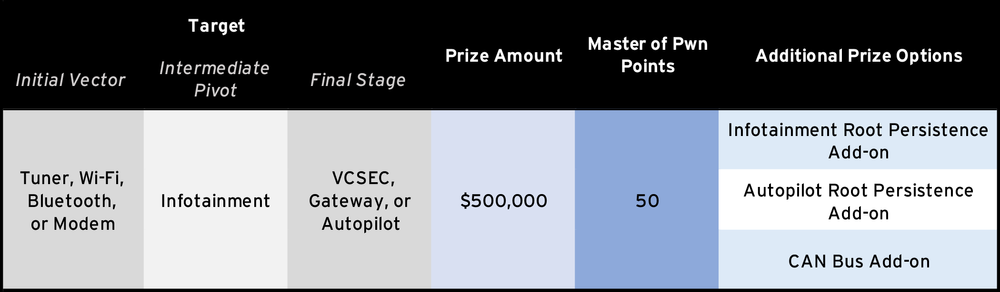
In addition to the vehicle itself and $500,000, contestants can go for the additional options to raise the payout to $700,000. This represents the single largest target in Pwn2Own history. If someone is able to do this, it would also mean 70 total Master of Pwn points, which is nearly insurmountable. Here’s some additional info on the optional add-ons.
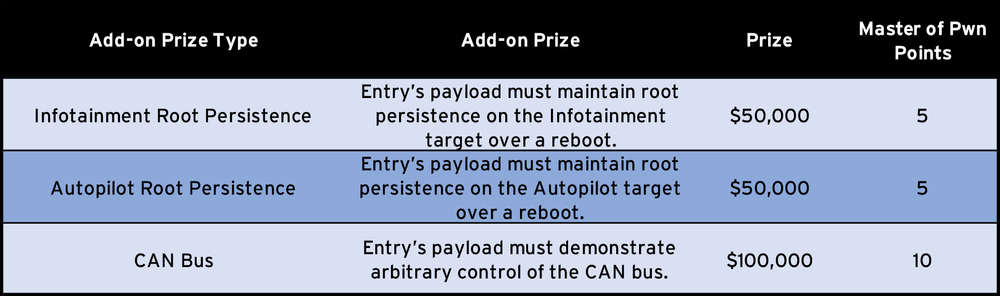
Again, it’s hard to express the difficulty in completing such a demonstration, but we’re certainly hopeful someone is able to show off their exploit skills.
Tier 2 is not quite as complex but would still require the attacker to pivot through some of the vehicle’s sub-systems. This level requires the contestant to get arbitrary code execution on two different sub-systems in the vehicle, which is certainly a difficult challenge. If you include the optional targets, the largest payout for Tier 2 would be $500,000. A wining entry in Tier 2 would still be a pretty impressive and exciting demonstration, and includes driving off with the Model 3.
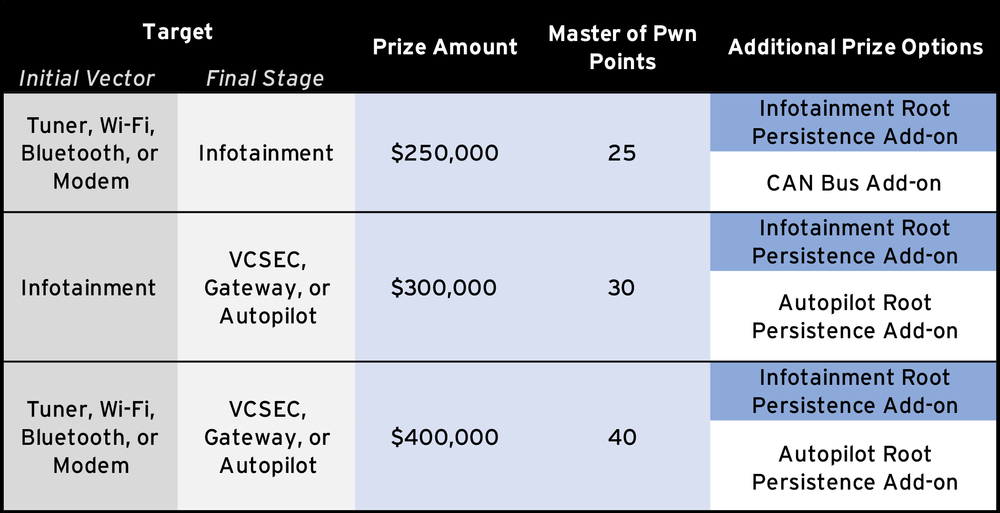
The targets in Tier 3 are just as difficult, but you only need to compromise one sub-system for a win here, which is still no easy task. Not every instance within Tier 3 includes winning the car. To drive away with a Tier 3 prize, a contestant would need to target one of the entries marked “Vehicle Included” in the table below.
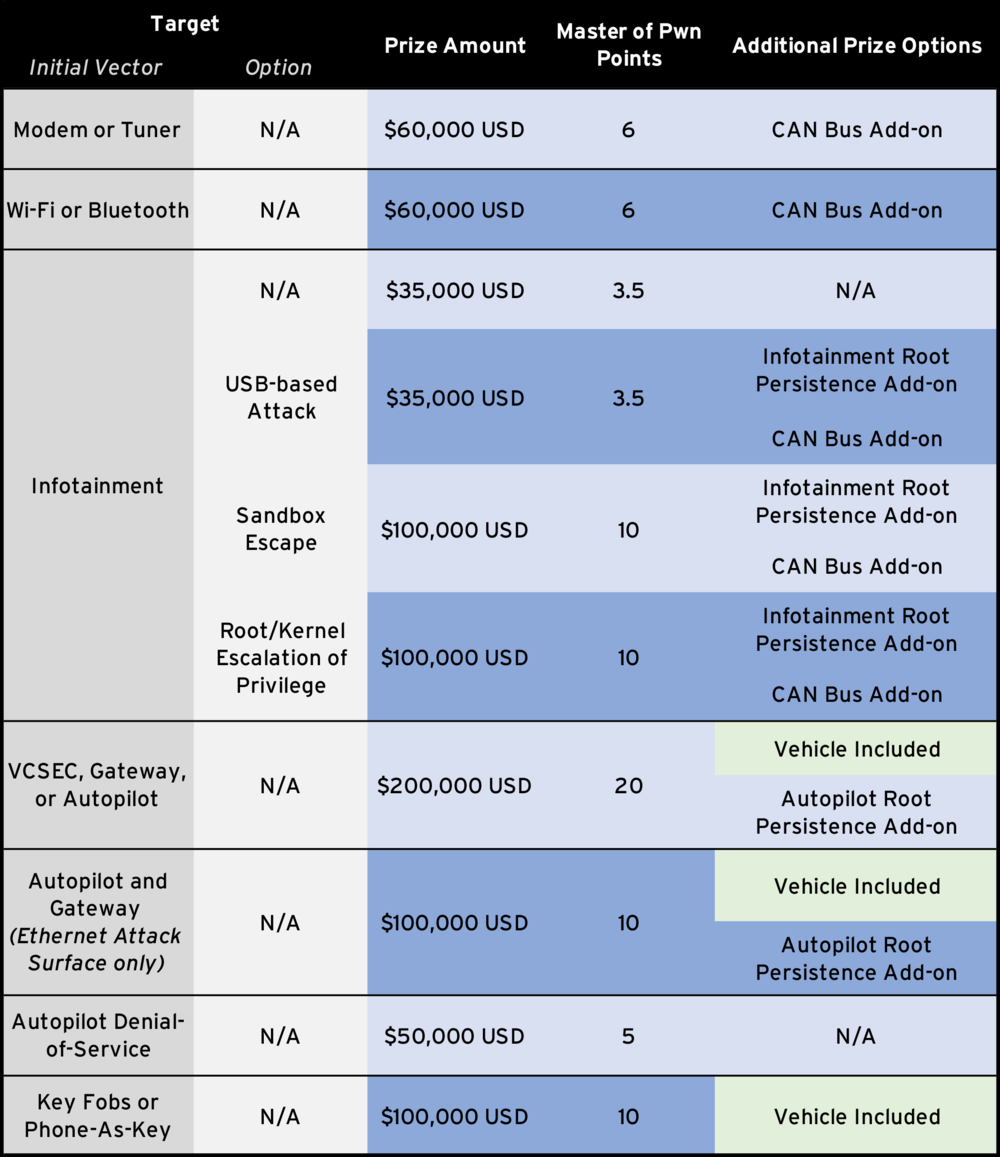
Entries against Modem or Tuner, Wi-Fi or Bluetooth, and Gateway, Autopilot, or VCSEC targets must achieve code execution by communicating with a rogue base station or other malicious entity. Entries against the Infotainment target must be launched from the target under test and must achieve code execution by browsing to malicious content. In Tier 1 and Tier 2, man-in-the-middle browser attacks against the Infotainment system are not allowed. Any Infotainment entry that leverages vulnerabilities in the built-in browser must be chained with a sandbox escape or a root/kernel privilege escalation. USB-based attacks in the Infotainment category must target the USB port that passengers would routinely plug into that is openly exposed on the center console. Any other exposed USB ports are not in scope for this contest. Entries against the Key Fobs or Phone-as-Key target must achieve code execution, arbitrary vehicle unlock, or arbitrary vehicle start using protocol-related weaknesses. Entries related to Key Fob relay or rolljam attacks are not allowed.
As always, please refer to the rules for complete details and don’t hesitate to email your specific questions to us ahead of the contest.
Probably the most traditional category for Pwn2Own, the Web Browser category also sees a few changes this year. Now that Microsoft Edge has both an EDGEHTML-based version and a Chromium-based version, both are included as targets. This presents an interesting opportunity – and an interesting challenge. If a single entry is able to compromise both Google Chrome and Microsoft Edge (Chromium), the contestant will receive an additional $50,000 and 5 more Master of Pwn points.
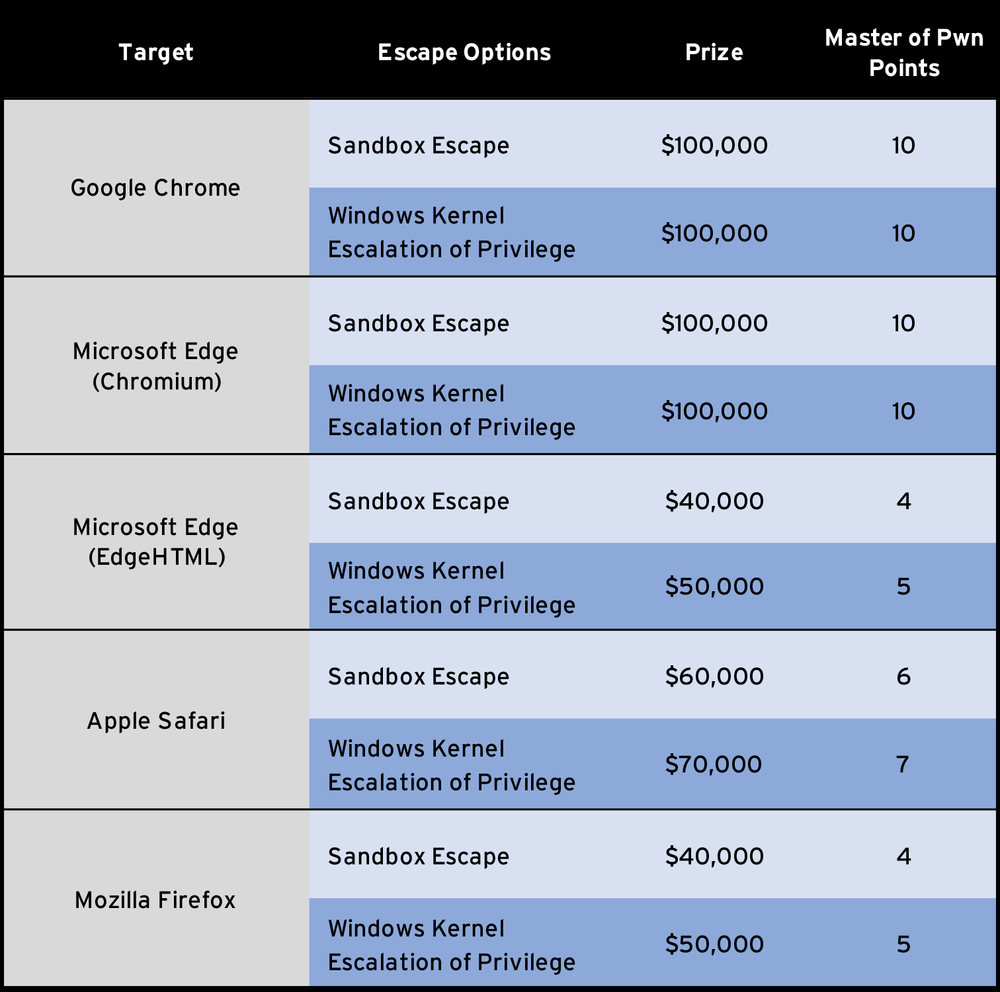
In this category, the Windows-based targets will be running in a VMware Workstation virtual machine. Consequently, all browsers except Safari are eligible for a VMware escape add-on. If a contestant is able to compromise the browser in such a way that also executes code on the host operating system by escaping the VMware Workstation virtual machine, they will earn themselves an additional $70,000 and 7 more Master of Pwn points.
This category was introduced several years ago and continues to produce some of the most interesting research of the conference. It’s always awe-inspiring (and just a tad terrifying) to see an exploit escape from a virtual machine and execute code on the host OS. Microsoft Hyper-V headlines this category, with VMware Workstation, VMware ESXi, and Oracle VirtualBox as the other targets.
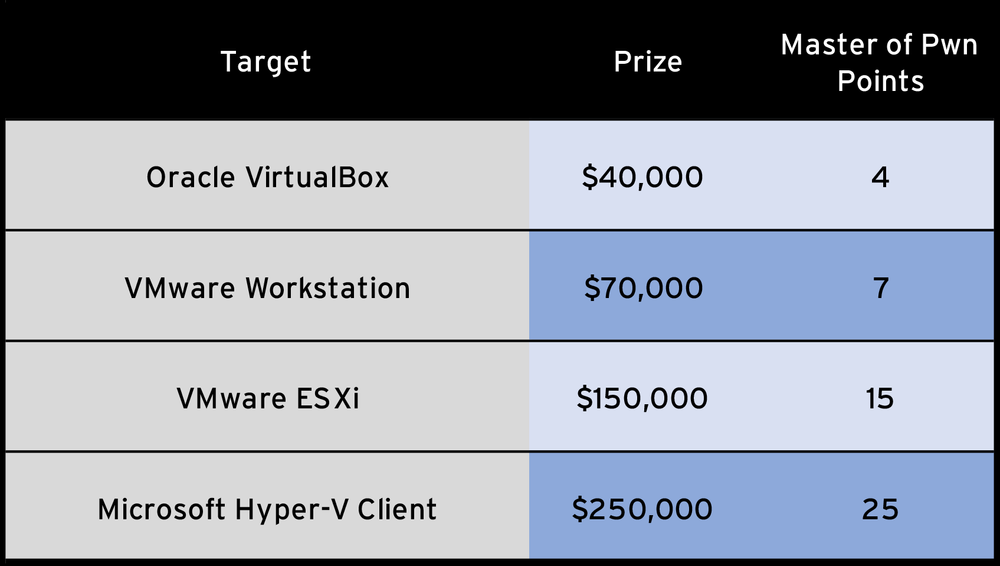
For Oracle VirtualBox, VMware Workstation, and Microsoft Hyper-V Client, both the guest and the host operating system will be running Microsoft Windows 10 19H2 x64. For VMware ESXi, the guest operating system will be running Microsoft Windows 10 19H2 x64.
There’s an add-on bonus in this category as well. If a contestant can escape the guest OS, then escalate privileges on the host OS through a Windows kernel vulnerability (excluding VMware ESXi), they can earn an additional $40,000 and 4 more Master of Pwn points.
Enterprise Applications Category
Applications remain at the heart of our day-to-day computing lives, and for 2020, we’re including two of the most popular apps for this category. This year, Adobe Reader and Microsoft Office 365 Plus encompass this category. The Office targets will be running Microsoft Office 365 Professional Plus x64 (Monthly Channel) on Windows 10 x64. Microsoft Office-based targets will have Protected View enabled. Adobe Reader will have Protected Mode enabled.

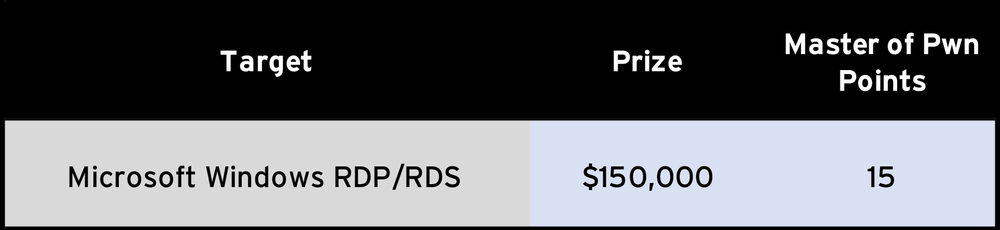
Similar to last year, the Server-Side category contains only Microsoft Windows RDP as most of our other server-side targets are represented in our Targeted Incentive Program. It’s been a fascinating year for RDP bugs, so it will be interesting to see if anyone brings a Bluekeep-like exploit to demonstrate. If they do, they’ll earn themselves $150,000 and 15 Master of Pwn points.
Local Escalation of Privilege Category
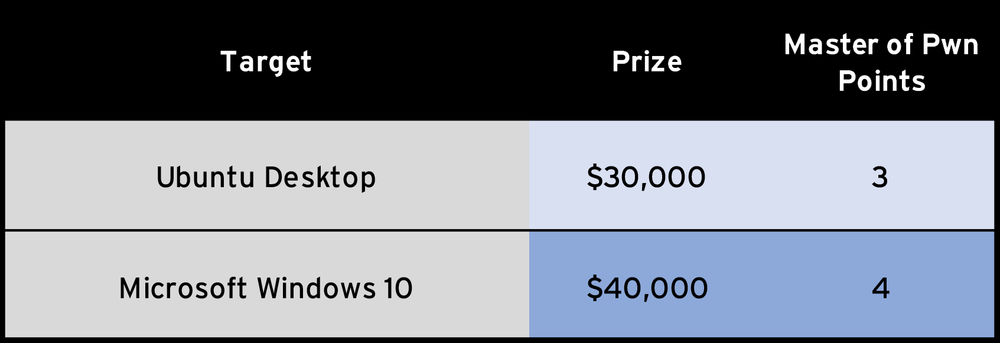
This category is one we’ve included in the past, although it has had a brief absence from the contest. This category focuses on attacks that originate from a standard user and result in executing code as a high-privileged user. This is a common tactic for malware and ransomware, so these bugs are highly relevant. In this category, the entry must leverage a kernel vulnerability to escalate privileges. We picked two of the most popular operating systems for this category: Ubuntu Desktop and Microsoft Windows 10.
Conclusion
The complete rules for Pwn2Own 2020 are found here. As always, we encourage entrants to read the rules thoroughly if they choose to participate. If you are thinking about participating but have a specific configuration or rule-related questions, email us. Questions asked over Twitter or other means are not guaranteed to be answered. Registration is required to ensure we have sufficient resources on hand at the event. Please contact ZDI at zdi@trendmicro.com to begin the registration process. Registration closes at 5 p.m. Pacific Time on March 13, 2020.
Be sure to stay tuned to this blog and follow us on Twitter for the latest information and updates about the contest. We look forward to seeing everyone in Vancouver, and we hope someone again has a sweet ride home from this year’s Pwn2Own competition.
With special thanks to our Pwn2Own 2020 Partners Tesla and Microsoft

Thanks also to our Pwn2Own 2020 Sponsor VMware

...


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren