📚 Aaia - AWS Identity And Access Management Visualizer And Anomaly Finder
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
Aaia (pronounced as shown here ) helps in visualizing AWS IAM and Organizations in a graph format with help of Neo4j. This helps in identifying the outliers easily. Since it is based on neo4j , one can query the graph using cypher queries to find the anomalies.
Aaia also supports modules to programatically fetch data from neo4j database and process it in a custom fashion. This is mostly useful if any complex comparision or logic has to be applied which otherwise would not be easy through cypher queries.
Aaia was initially intended to be a tool to enumerate privelege esclation possibilities and find loop holes in AWS IAM. It was inspired from the quote by @JohnLaTwC
"Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win."
Why the name "Aaia" ?
Aaia in Tamil means grandma. In general, Aaia knows everything about the family. She can easily connect who is related to whom; and how ;and give you the connection within a split second. She is a living graph database. :P
Since "Aaia" (this tool) also does more or less the same, hence the name.
Installation
Install the neo4j Database
Instructions here
Setup the username , password and bolt connection uri in Aaia.conf file. An example format is given in Aaia.conf file already.
Install OS dependency
Debian :-
apt-get install awscli jq
Redhat / Fedora / Centos / Amazon Linux :-
yum install awscli jq
Note:
These packages are needed for Aaia_aws_collector.sh script. Ensure these packages are present in the base system from where the collector script is being run.
Clone this repository
git clone https://github.com/rams3sh/Aaia
cd Aaia/
Create a virtual environment
python3 -m venv env
Activate the virtual environment
source env/bin/activate
Note: Aaia depends on pyjq library which is not stable in windows currently. Hence Aaia is not supported for Windows OS.
Install the dependencies
python -m pip install -r requirements.txt
Using Aaia
Setting up Permissions in AWS
Aaia would require following AWS permissions for collector script to collect relevant data from AWS
iam:GenerateCredentialReport
iam:GetCredentialReport
iam:GetAccountAuthorizationDetails
iam:ListUsers
iam:GetUser
iam:ListGroups
iam:ListRoles
iam:GetRole
iam:GetPolicy
iam:GetAccountPasswordPolicy
iam:GetAccountSummary
iam:ListAccountAliases
organizations:ListAccountsForParent
organizations:ListOrganizationalUnitsForParent
organizations:DescribeOrganization
organizations:ListRoots
organizations:ListAccounts
organizations:ListTagsForResource
organizations:ListPolicies
organizations:ListTargetsForPolicy
organizations:DescribePolicy
organizations:ListAWSServiceAccessForOrganizationEnsure the permissions are available to the user / role / any aws principal which will be used for collection of data for the collector script.
Collecting data from AWS
Ensure you have aws credentials configured. Refer this for help.
Once the crendential is setup.
Run:-
./Aaia_aws_collector.sh <profile_name>Note:-
In case of a requirement where data has to be collected from another instance; copy "Aaia_aws_collector.sh" file to the remote instance , run it and copy the generated "offline_data" folder to the Aaia path in the instance where Aaia is setup and carry on with following steps. This will be helpful in cases of consulting or client audit.
Loading the collected data to Neo4j DB
python Aaia.py -n <profile_name> -a load_dataNote:
Please ensure you do not have profile as "all" in the credentials file as it may conflict with the argument. :P
Now we are ready to use Aaia.
Audit IAM through a custom module
As of now , a sample module is given as a skeleton example. One can consider this as a reference for building custom modules.
python Aaia.py -n all -m iam_sample_auditThanks to
Aaia is influenced and inspired from various amazing open source projects. Huge Shoutout to :-
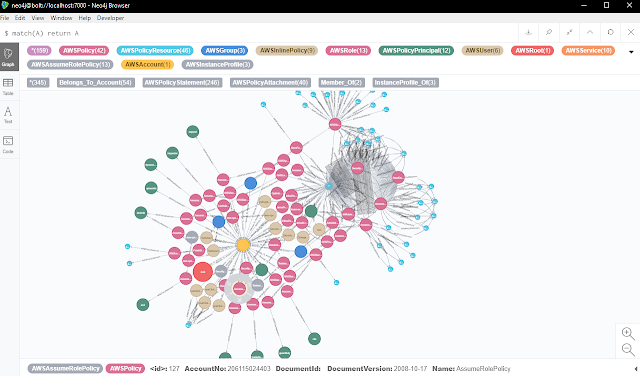
Aaia in Action
Screenshots
A sample visual of a dummy AWS Account's IAM
A sample visual of a result of a cypher query to find all relations of a user in AWS IAM
TO DO
- Write a detailed documentation for understanding Aaia's Neo4j DB Schema
- Write a detailed documentation for developing custom modules for Aaia
- Write custom modules to evaluate 28 AWS privelege escalation methods identified by RhinoSecurity.
- Provide a cheatsheet of queries for identifying simple issues in AWS IAM
- Extend Aaia to other cloud providers.


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren